Math Is Fun Forum
You are not logged in.
- Topics: Active | Unanswered
#2151 2024-05-15 16:33:34
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2153) Apple Juice
Details
When apples are juiced, their hydrating quality is maximized, and some plant compounds are retained. However, juicing reduces other benefits of whole apples, including fiber and the ability to satisfy hunger.
Whole apples are an extremely healthy food, but apple juice has pros and cons.
Here are 4 benefits and 5 downsides of drinking apple juice.
1. Supports hydration
Apple juice is 88% water and tastes good. This makes it easy to consume — especially for those who are sick and at an increased risk of dehydration.
In fact, some pediatricians recommend half-strength apple juice — a mix of half juice, half water — for sick kids who are mildly dehydrated and at least one year old.
In a study of mildly dehydrated children with diarrhea and vomiting, those offered diluted apple juice were 6.5% less likely to need fluids delivered via their veins than those given a medicinal electrolyte drink.
Though electrolyte drinks are specially formulated to rehydrate, some children don’t like the taste and won’t drink them. They’re also relatively expensive.
Diluted apple juice is a practical and pleasant alternative for kids, as well as adults.
Be sure to drink diluted juice to rehydrate, as the high sugar content of full-strength juice can draw excess water into your gut and worsen diarrhea — particularly during recovery from illness.
In more severe cases of dehydration, medicinal electrolyte drinks are still advised. Though the amount of potassium in apple juice is similar to electrolyte drinks, it has little sodium, which is also lost via bodily fluids when you’re sick.
Summary
Apple juice is high in
* water and tastes good, making it a good choice for hydrating. To avoid side
* effects, dilute to half-strength when using it to rehydrate after an illness.
2. Contains beneficial plant compounds
Apples are rich in plant compounds, particularly polyphenols. While the majority of these compounds are in the peel, some from the apple flesh are retained in the juice.
These plant compounds may protect your cells from inflammation and oxidative damage. Both of these processes are underlying factors in chronic conditions, including certain cancers and heart disease.
In one study, healthy men drank a 2/3 cup (160 ml) of apple juice, then scientists drew their blood. Oxidative damage in their blood was suppressed within 30 minutes of drinking the juice, and this effect continued for up to 90 minutes.
For more polyphenols, opt for cloudy juice — which contains pulp — rather than clear, which has the pulp removed.
One analysis found that cloudy apple juice had up to 62% more polyphenols than clear juice.
The majority of store-bought apple juice is clear in appearance, meaning you can easily see through it. Organic varieties are more commonly available in the cloudy form.
Summary
Apple juice contains
* plant compounds called polyphenols, which may help protect your cells from
* disease-promoting oxidative stress and inflammation. Cloudy juice with pulp is
higher in polyphenols than clear juice.
3. May support heart health
Plant compounds — including polyphenols — in apple juice may be particularly beneficial for heart health.
Polyphenols may prevent LDL (bad) cholesterol from becoming oxidized and building up in your arteries. Higher levels of oxidized LDL are linked to an increased risk of heart attack and stroke.
One study observed that when healthy adults drank 1 1/2 cups (375 ml) of clear apple juice daily for 6 weeks, their LDL (bad) cholesterol was 20% more resistant to oxidation compared to the start of the study.
Additionally, when healthy women drank 1 1/4 cups (310 ml) of clear apple juice, the antioxidant activity of their blood increased nearly 11% within 1 hour of drinking the juice, compared to a placebo drink.
This boost in antioxidant activity means more potential protection from heart disease. Still, more human studies are needed to confirm these heart health benefits.
Summary
Human studies suggest
* drinking apple juice may increase antioxidant activity in your blood and help
protect LDL (bad) cholesterol from oxidation. This may reduce your risk of
heart disease.
4. May protect your brain as you age
Preliminary studies suggest that apple juice may support brain function and mental health as you age.
Some of this protection may be due to the antioxidant activity of the polyphenols found in the juice. They may shield your brain from damage by unstable molecules called free radicals.
In a series of studies, older mice were given daily apple juice that was equivalent to 2‒3 cups (480‒720 ml) for a human. When the mice consumed the juice for one month, they:
* performed significantly better on
maze-based memory tests, compared to a control group that didn’t receive
the juice
* maintained brain levels of
acetylcholine, a nerve messenger that’s important for memory and good
mental health and that tends to decline in aging — as was the case in the
control group in this study
* suppressed an
increase in beta-amyloid protein fragments in the brain, which are
associated with brain damage in Alzheimer’s disease
Additionally, when people with Alzheimer’s disease drank 1 cup (240 ml) of apple juice daily for 1 month, their behavioral and mental symptoms — like anxiety, restlessness, and false beliefs — improved by 27%. However, memory and problem solving didn’t improve.
Further human studies are needed to confirm the benefits of apple juice for brain function and clarify how much would be needed for this purpose.
Summary
Animal studies observe
that apple juice may help protect memory and other aspects of brain health in
aging. Preliminary human research suggests that it may improve behavior and
mental health in Alzheimer’s disease.
5 Downsides of apple juice
Juicing apples results in the loss of some benefits and creates potential health risks.
Here are the top 5 concerns related to drinking apple juice, along with ways to overcome some of them.
1. May contribute to weight gain
If you drink apple juice, portion control is essential. A 1-cup (240-ml) serving has 114 calories, while a medium-size apple has 95 calories.
The juice can be consumed faster than a whole apple, which can cause you to take in a large number of calories over a short period of time.
Additionally, juice isn’t particularly good at satisfying hunger or helping you feel full. This may lead you to consume excess calories.
In one study, adults were given a whole apple, applesauce, or apple juice in equal amounts based on calories. Whole apples satisfied their hunger best. Juice was the least filling — even when fiber was added to it.
For these reasons, the risk of taking in too many calories and gaining weight from drinking juice is greater, compared to eating whole apples. This is true for both adults and children.
The American Academy of Pediatrics recommends the following daily juice limits:
Age : Juice limit
1–3 : 1/2 cup (120 ml)
3–6 : 1/2–3/4 cup (120–175 ml)
7–18 : 1 cup (240 ml)
One cup (240 ml) is also the recommended daily limit for adults.
2. Low in vitamins and minerals
A 1-cup (240-ml) serving of apple juice is not a good source of any vitamins or minerals, meaning it doesn’t supply at least 10% of the Reference Daily Intake (RDI) for any micronutrient.
That said, vitamin C — or ascorbic acid — is commonly added. In many cases, apple juice is fortified to provide 100% or more of the RDI for vitamin C per serving.
If not fortified, apple juice provides around 2% of the RDI for this vitamin per serving. For comparison, one medium apple averages 9% of the RDI.
If you eat a variety of whole fruits and vegetables, you can easily meet your quota for vitamin C without drinking fortified juice.
3. High in sugar — low in fiber
Choose 100% juice varieties rather than drinks that are a blend of apple juice, added sugar, and water.
Still, virtually all of the calories in 100% apple juice come from carbs — mostly from fructose and glucose, two naturally-occurring sugars.
At the same time, a 1-cup (240-ml) serving of juice — whether clear or cloudy — supplies only 0.5 grams of fiber.
For comparison, a medium apple with the peel has 4.5 grams of fiber — or 18% of the RDI — for this nutrient.
Fiber, as well as protein and fat, helps slow digestion and promotes a more moderate rise in blood sugar. The combination of high sugar and low fiber in the juice can spike your blood sugar.
If you drink apple juice, pair it with something that contains protein and healthy fat to reduce its impact on your blood sugar.
For example, when healthy adults ate a breakfast of apple juice, bread, and peanut butter, their rise in blood sugar was 30% less compared to the same meal without peanut butter.
4. Encourages tooth decay
Drinking fruit juice is linked to tooth decay. Bacteria in your mouth consume the sugars in juice and produce acids that can erode tooth enamel and lead to cavities.
In a test-tube study that assessed the dental effects of 12 different types of fruit juice, apple juice was found to erode tooth enamel the most.
If you drink apple juice, avoid swishing it around in your mouth. The longer your teeth are exposed to sugar, the more likely you’ll get cavities. Using a straw may also reduce your risk of tooth decay.
5. Contaminated with pesticides
If you drink nonorganic juice, pesticide contamination is another concern. Pesticides are chemicals used to protect crops from insects, weeds, and mold.
When the U.S. Department of Agriculture tested 379 samples of nonorganic, 100% apple juice, about half of them contained detectable levels of at least one pesticide.
Though these residues were below the limits set by the U.S. Environmental Protection Agency, children are more vulnerable to pesticide exposure than adults. If your child regularly drinks apple juice, it’s probably best to choose organic.
Organic juice is also preferable for adults, as it’s uncertain how long-term exposure to small amounts of pesticides may increase your risk of certain cancers, fertility problems, or other health concerns
Summary
You should limit apple
juice in your diet because it isn’t very filling, is high in sugar, encourages
tooth decay, and is low in vitamins, minerals, and fiber. Nonorganic juice is
also commonly contaminated with pesticides.
The bottom line
Apple juice can be useful for rehydrating when you’re sick. Its disease-fighting plant compounds may also protect your heart and brain as you age.
However, apple juice is not very filling compared to whole apples, nor does it offer much fiber, vitamins, or minerals.
Still, if you really like it, choose cloudy, organic juice with the pulp to get more beneficial plant compounds and avoid pesticide contamination.
Due to its high calorie content, be sure to enjoy juice in moderation.
Additional Information
Apple juice is a fruit juice made by the maceration and pressing of an apple. The resulting expelled juice may be further treated by enzymatic and centrifugal clarification to remove the starch and pectin, which holds fine particulate in suspension, and then pasteurized for packaging in glass, metal, or aseptic processing system containers, or further treated by dehydration processes to a concentrate.
Due to the complex and costly equipment required to extract and clarify juice from apples in large volume, apple juice is normally produced commercially. In the United States, unfiltered fresh apple juice is made by smaller operations in areas of high apple production, in the form of unclarified apple cider. Apple juice is one of the most common fruit juices globally, with world production led by China, Poland, the United States, and Germany.
Production
Apples used for apple juice are usually harvested between September and mid-November in the Northern Hemisphere and between February and mid-April in the Southern Hemisphere. A common cultivar used for apple juice is the McIntosh. Approximately two medium McIntosh apples produce around 200 millilitres (7.0 imp fl oz; 6.8 US fl oz) of juice. After the apples are picked, they are washed and transported to the processing facility. The apples are then pressed and juiced right away to avoid spoilage. Depending on the company and end-product, the apples can be processed in different ways before pressing. Apple juice is then filtered, with the number of solid particles remaining partly defining the difference between apple juice and apple cider. In cases where the apple juice is treated enzymatically, the typical class of enzymes used are pectinases.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2152 2024-05-16 14:39:53
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2154) Transmission and Distribution Losses
Gist
Electric power transmission and distribution losses include losses in transmission between sources of supply and points of distribution and in the distribution to consumers, including pilferage.
Details
Transmission loss (TL) in general describes the accumulated decrease in intensity of a waveform energy as a wave propagates outwards from a source, or as it propagates through a certain area or through a certain type of structure.
It is a terminology frequently used in radio communication, twisted pair systems (PTSN, Ethernet, etc), optics and acoustics. Measures of TL are very important in the industry of acoustic devices such as mufflers and sonars.
Applications
Transmission loss may refer to a more specific concept in one of the fields below:
* Transmission loss in electrical engineering describes the decrease of electrical power along an electrical cable. The term has its origins in telephony.
* Transmission loss in duct acoustics describes the acoustic performances of a muffler like system.
* Transmission loss in room acoustics describes the decrease of sound intensity that is reduced by a wall or other structure at a given frequency.
* Transmission loss in underwater acoustics describes the decrease of sound intensity that is reduced by a bubble curtain or other damping structure at a given frequency. The same term is sometimes used to mean propagation loss, which is a measure of the reduction in sound intensity between the sound source and a receiver, defined as the difference between the source level and the sound pressure level at the receiver.
As electricity travels through power lines, a proportion of energy is lost as heat, due to the resistance in the lines. The losses are higher, the greater the distance the electricity travels and the lower the voltages of the line.
Importance of distribution losses
Loss factors directly impact the cost of electricity faced by all consumers.
Distributors need to calculate and allocate for losses arising on their networks, so that the reconciliation process can account for these losses.
The reconciliation loss factor is used in:
* the reconciliation process by the reconciliation manager to allocate volumes of electricity at grid exit points (GXPs) to participants (both buyers and sellers from/to the clearing manager)
* the retail pricing process by retailers for the sale of electricity to consumers
* in the case of GXP charging networks, the calculation of network charges.
Types of losses
There are four types of losses within a network:
Technical losses
The difference between energy actually injected into a network and energy actually delivered to points of connection. These losses can result from the inevitable physical loss of electricity in networks.
Non-technical losses
The difference between the volume of energy actually conveyed at points of connection and the volume of energy reported as conveyed at the same points of connection. These losses can result from theft, metering errors and data handling errors.
Reconciliation losses
The difference between reported energy injected into a network and the reported energy extracted from the network. Reconciliation loss is the combination of technical and non-technical loss.
Unaccounted for electricity
This is calculated from the difference between reported energy injected into a network and the reported energy extracted from the network after it has been adjusted for losses.
It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2153 2024-05-17 14:11:05
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2155) Geometry Box
Summary
A geometry box is a set of various instruments required for basic geometric diagrams and graphs. It consists of instruments like a compass, divider, ruler, set squares, and protractor. These instruments are crucial for geometry classes.
Let us understand the usage of various instruments in the geometry box.
* A ruler is used to measure the length and width of an object. It is also used to draw lines as per the needs.
* The next crucial instrument in a geometry box is a compass. Math Students can learn to draw circles using a compass.
* Another crucial tool is a divider that measures the distance between two points. The significant advantage of this tool is that it gives accurate results.
* A protractor is a tool to measure the angle between two intersecting lines.
* The last set of tools includes set-squares. The box has two set squares of triangular shape.
These tools are significant for students learning geometry. Geometry tools are of great help for people in the design field. The tools let you design blueprints in the absence of a computer. Moreover, the instruments ensure that your angles and distances are on point.
Geometry plays a crucial role in the life of every student. You can draw accurate angles and lines using the geometry box. However, learning the right tricks and tips are crucial for accurate measurements. Students can use the best geometry sets to make the right measurements. The tools are vital when appearing for mathematics tips classes and examinations. Students can practice sums on geometry using worksheets and online learning materials.
Details
Geometry box, also known as a math set or a drawing kit, is a collection of essential tools used for various geometrical and mathematical tasks. It is commonly used by students, architects, engineers, artists, and anyone involved in drawing, designing, or mathematical work. A typical geometry box contains several tools neatly organized in a compact box or case. The specific contents of a geometry box can vary, but some common items typically found in a geometry box include:
Compass: A tool used for drawing circles and arcs of various sizes.
Divider: Similar to a compass but with two pointed ends, used for measuring and transferring distances.
Protractor: A semi-circular instrument used for measuring angles in degrees.
Set Square (Triangle): Triangular rulers with different angles (typically 30°, 45°, and 60°) used for drawing lines at specific angles.
Scale Ruler: A ruler with various scales (e.g., centimeters, millimeters, inches) for measuring and drawing accurate straight lines.
Pencil: Essential for drawing and sketching.
Eraser: Used to remove pencil marks and mistakes.
Sharpener: For sharpening pencils.
What is Geometry Box?
A geometry box is a set of basic equipment required for regular use in basic geometrical diagram and graphs. The basic geometry box consists of a compass, a 15cm ruler, a divider, 2 set squares and a protractor.
A geometry box, also known as a geometry set or a math set, is a collection of essential tools used for various geometrical and mathematical tasks. It is a common tool used by students, artists, architects, engineers, and anyone involved in drawing, designing, or mathematical work.
What is the use of instruments in geometry box?
The instruments in a geometry box serve specific purposes and are used to perform various geometrical and mathematical tasks. Each tool has its unique function, and together, they help students, artists, architects, engineers, and others to draw accurate shapes, measure angles, and perform other geometric operations. Here are the uses of some common instruments found in a geometry box:
* Compass: The compass is used to draw circles and arcs of various sizes. It consists of two arms—one with a pointed end to act as the center and the other with a pencil to draw the circle or arc.
* Divider: Similar to a compass, the divider has two pointed ends and is used to measure and transfer distances. It helps in replicating lengths or distances on paper.
* Protractor: The protractor is a semi-circular instrument with a scale of angles in degrees. It is used to measure and draw angles accurately.
* Set Square (Triangle): Set squares are triangular rulers with different angles (30°, 45°, and 60°). They are used for drawing lines at specific angles and constructing geometric shapes.
* Scale Ruler: The scale ruler has various scales (e.g., centimeters, millimeters, inches) and is used for measuring lengths and drawing straight lines of specific lengths.
Who invented geometry box?
The concept of a geometry box, as we know it today, is not attributed to a single inventor. Instead, it evolved over time as various tools used for geometric and mathematical tasks were developed and organized into a single kit.
The individual components of a geometry box, such as compasses, rulers, and protractors, have a long history of development, and their origins can be traced back to ancient civilizations. For example:
Geometric Tools: Description And Uses - Maths
Geometric tools are essential instruments used in mathematics to aid in drawing precise geometric shapes, measuring angles, and performing various mathematical operations. These tools are commonly found in geometry boxes or math sets and are used by students, mathematicians, engineers, architects, artists, and other professionals working with geometric concepts. Here are some common geometric tools, along with their descriptions and uses in mathematics:
* Compass: A compass consists of two arms, one with a pointed end and the other with a pencil. It is used to draw circles and arcs of various sizes. In geometry, circles and arcs are fundamental shapes used in constructions and proofs.
* Divider: Similar to a compass, a divider has two pointed ends and is used to measure and transfer distances. It helps in replicating lengths or distances on paper accurately.
* Protractor: A protractor is a semi-circular instrument with a scale of angles in degrees. It is used to measure and draw angles precisely. Protractors are crucial for understanding angles and angle measurements in geometric shapes.
* Set Square (Triangle): Set squares are triangular rulers with different angles (usually 30°, 45°, and 60°). They are used for drawing lines at specific angles and constructing geometric shapes, such as triangles, squares, and hexagons.
* Scale Ruler: A scale ruler has various scales (e.g., centimeters, millimeters, inches) and is used for measuring lengths and drawing straight lines of specific lengths. Scale rulers help maintain proportional accuracy in drawings.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2154 2024-05-18 14:58:48
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2156) Mango Juice
Summary
Mangoes, indigenous to India, Pakistan, Bangladesh and Southeast Asia, areis known for itstheir delectable taste and flavour. Grown across numerous varieties, the sultan of summer contains many useful nutrients that keep one healthy, content and cheerful. From the youngest to the oldest in the family, mango juice benefits all across ages. No wonder, it has been titled, the king of fruits.
Mango continues its legacy to remain in the top charts of every Indian household. Considered the national fruit of our country, it is known for its finger licking taste, beautiful odour, usefulness in rituals and providing shelter and shadow to human and animals. Apart from India, Mango is also the national fruit of Pakistan and Philippines. In Bangladesh, a mango tree is considered to be the national tree. The popularity of this fruit is always at its peak for the innumerable mango fruit benefits.
Details
Mango juice is just what it sounds like, juice made from mangos. The liquid from mangos can be pretty thick – if you’ve ever drank a can of mango nectar, you know what I mean. So to make mango juice, we add water to achieve an authentic “juice” consistency.
Recipe Ingredients
Mangos – Sweet and fleshy, this fruit is great to snack on, but it also makes a fantastic drink!
Sugar – This ingredient is optional, but you can incorporate it to dial up the sweetness if you want to.
Mint Leaves – This herb makes for a pretty garnish and is also the secret to my perfect sugar syrup. ?
How to Make Mango Juice
Start the Simple Syrup – Combine water, sugar, and mint leaves in a small saucepan. Bring to a boil, stirring until sugar dissolves. Simmer for one minute. Remove from the heat and let syrup steep for about 30 minutes.
Peel and Slice Mango – Slice the sides along the mango seed. Cut the mango flesh in a grid-like pattern without going through the mango skin. Detach the flesh from the skin with a large spoon and scoop the cubes out. For more tips on doing this step, see my guide on how to cut a mango.
Puree – Transfer the mango flesh and water to a blender or food processor and blend until smooth.
Finishing Touches – Pour the mango juice into a jar. Next, add the sugar syrup to taste. This step is optional, and the amount of sugar syrup you use is entirely up to you. Stir to combine.
Serve with ice cubes and garnish with mint leaves. Breathe deeply and enjoy!!!
Recipe Variations
Make your mango juice extra tropical by substituting the water with coconut water, orange juice, pineapple juice, or any other juice you love.
To make mango nectar instead of juice, leave the water out and only add sugar syrup. The finished product will be a much thicker and sweeter mango drink.
Make a mango smoothie by adding milk instead of water. Creamy and delicious! ?
Tips and Tricks
* With this mango juice recipe, consistency is totally up to you. Add more water if you would like a thinner juice.
* If you choose to add sugar syrup, do so a little at a time and taste the juice as you go until you reach your desired sweetness level. You can always add more sugar syrup if it isn’t sweet enough, but it will be hard to take it out if you add too much.
Make-Ahead Instructions
Mango juice stays fresh in the fridge for 3-5 days, so you can make it a few days in advance if you’d like. You can even freeze mango juice. It will keep good for three months in the freezer, so technically, you can make it way in advance if you’d like.
Serving and Storage Instructions
Serve mango juice cold! Add a few cubes of ice, give the glass a stir, and serve it up right away.
Store mango juice in a pitcher or jar with a lid in the fridge. You can freeze mango juice in any airtight container. I like to use ziplock bags personally.
When you are ready to use frozen mango juice, simply take it out of the freezer the night before. Once it’s thawed, you can serve it immediately.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2155 2024-05-19 00:12:59
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2157) Grape Juice
Details
Grape juice is a beverage known for its vibrant color and sweet, slightly tart flavor.
Many people consider it a healthy alternative to sugary beverages, like soda. In fact, according to the most recent Dietary Guidelines for Americans, 100% fruit juice can be enjoyed as part of a balanced diet.
However, due to its content of sugar and calories, you may wonder if grape juice is as healthy as fresh fruit.
This article explores the nutritional content, benefits, and downsides of grape juice, so you can learn if it’s good for you.
Types of grape juice
There are several types of grape juice. They differ in nutritional content and which specific grapes they’re made from.
Purple grape juice is the most commonly available commercial variety. It features a dark color and is usually made from Concord grapes.
You can also purchase white grape juice, which is made from green-skinned grapes and boasts a slightly sweeter taste.
Some grape juice is labeled as 100% juice, meaning that all the ingredients are extracted from fruits or vegetables.
Other varieties are labeled as juice from concentrate. That means that most of the water has been removed, resulting in a more concentrated product.
Grape juice is also featured in many juice math, some of which contain a blend of several types of fruit.
Grape juice may be sweetened or unsweetened. Sweetened grape juice contains added sugars, like high fructose corn syrup. Added sugar can be found listed on the ingredients label.
SUMMARY
There are several types of grape juice available. They differ depending on whether they’re sweetened, the types of grapes used, and whether they’re made from concentrate, a blend of fruits, or 100% fruit juice.
Nutrients
Though grape juice is high in carbs and natural sugar, it’s also a good source of several nutrients, including vitamin C and manganese.
One cup (237 mL) of unsweetened purple grape juice contains the following nutrients:
Calories: 152
Protein: 1 gram
Fat: 0.3 grams
Carbs: 37.4 grams
Fiber: 0.5 grams
Vitamin C: 70% of the Daily Value (DV)
Manganese: 26% of the DV
Magnesium: 6% of the DV
Potassium: 6% of the DV
Copper: 5% of the DV
Many types of grape juice contain added ascorbic acid, also known as vitamin C. This nutrient is essential for immune function and skin health.
Grape juice is also rich in manganese, a mineral involved in bone formation and the production of certain neurotransmitters in your brain.
What’s more, grape juice contains several flavonoids and polyphenols. These are plant compounds that act as antioxidants to protect against oxidative stress and inflammation.
SUMMARY
Grape juice is high in carbs, but it also contains a good amount of vitamin C, manganese, and antioxidants in each serving.
Benefits
Grape juice has been associated with several health benefits. For example, it may promote the health of your heart, immune system, and digestive tract.
Enhances heart health
Thanks to its content of antioxidant compounds, several studies have found that grape juice could support heart health.
According to one review, the flavonoids found in Concord grape juice could help lower several risk factors for heart disease, including:
* inflammation
* plaque build-up in the arteries
* platelet aggregation
* cholesterol and triglyceride levels
In a small study with 25 women, drinking white grape juice daily for 30 days increased levels of HDL (good) cholesterol by 16% and decreased belly fat.
Similarly, a review reported that grape products, including grape juice, could significantly improve levels of total, LDL (bad), and HDL (good) cholesterol compared with a control. As such, it might help protect against heart disease.
Still, more high quality research is needed to better understand the juice’s effects on heart health.
Promotes immune function
Many varieties of grape juice are enriched with the micronutrient vitamin C.
Vitamin C can enhance immune function by reducing oxidative stress and supporting the function of your immune cells.
Getting enough vitamin C in your daily diet may reduce your susceptibility to illness and infection, including respiratory infections, like the common cold.
Grape juice is also a great source of antioxidants, like resveratrol, a compound that can reduce inflammation and regulate immune cells.
Supports digestive health
Some research has found that grape juice might support the health of your digestive system.
For instance, a recent study showed that taking a grape powder supplement — equivalent to about 3.4 ounces (100 mL) of grape juice — could increase the diversity of your beneficial gut microbiome to promote digestive health.
Several studies in animals have found similar results, noting that certain compounds and polyphenols extracted from grapes and grape juice could support the health of the gut microbiome.
Some types of grape juice also contain a small amount of fiber, with around 0.5 grams per cup (237 mL).
Although this is much less than the amount found in whole grapes, it can help you meet your daily needs for fiber, an essential nutrient that promotes regularity and digestive health.
SUMMARY
Some studies show that grape juice and its components could improve heart health, promote immune function, and support digestive health.
Downsides
Though grape juice can be enjoyed in moderation as part of a healthy diet, there are a few downsides to consider.
May increase blood sugar levels
Grape juice contains a high amount of natural sugars. Even unsweetened varieties pack 36 grams into each 1-cup (237-mL) serving.
Compared with whole fruits, fruit juice is also lower in fiber. Fiber slows the absorption of sugar into the bloodstream to stabilize blood sugar levels.
Several types are also sweetened with high amounts of added sugar. Studies show that increased intake of sugar-sweetened beverages may be linked to a higher risk of type 2 diabetes and impaired blood sugar control.
That said, unsweetened varieties may not have the same effects. Some studies show that drinking 100% fruit juice isn’t associated with higher blood sugar levels or an increased risk of type 2 diabetes.
Could contribute to weight gain
Grape juice is low in fiber, meaning that it doesn’t increase feelings of fullness to the same extent as whole fruits.
Studies show that liquids are less filling than solid foods. So, you might feel more hungry after drinking a glass of grape juice compared with eating fresh grapes.
Sugar-sweetened beverages, such as grape juice with added sugar, have also been linked to a higher risk of weight gain, overweight, and obesity among children and adults.
Additionally, some types of sweetened grape juice are high in calories and can contribute to weight gain if consumed in high amounts and if you don’t make other adjustments to your diet.
SUMMARY
Grape juice is low in fiber and some types contain added sugar, which could negatively impact blood sugar control. Certain varieties may also contribute to weight gain, especially if you don’t make other adjustments to your diet.
Should you drink grape juice?
Grape juice is a good source of several important vitamins, minerals, and antioxidants and can fit into a healthy, well-rounded diet.
Be sure to keep your intake moderate. While the Dietary Guidelines for Americans recommends limiting your intake to 4–10 ounces (118–296 mL) per day, other research shows that drinking 3.4–5 ounces (100–150 mL) per day may offer the most health benefits.
Ideally, choose unsweetened varieties made with 100% grape juice and steer clear of brands that contain added sugar like high fructose corn syrup.
Alternatively, opt for whole grapes instead. These contain the same beneficial nutrients as grape juice, along with a higher amount of fiber to support healthy blood sugar levels.
SUMMARY
Grape juice can be enjoyed in moderation as part of a balanced diet. Stick to unsweetened varieties made with 100% grape juice or opt for whole, fiber-rich grapes instead.
The bottom line
Grape juice is a good source of several important nutrients, including vitamin C, manganese, and antioxidants.
It’s also linked to several health benefits. For example, it may support heart health, immune function, and digestive health.
However, it’s also high in sugar and has less fiber than whole fruits. It could increase blood sugar levels or contribute to weight gain if consumed in large amounts.
Therefore, it’s best to stick to a moderate intake and select unsweetened varieties made with 100% grape juice whenever possible.
Alternatively, choose whole fruits instead to increase your fiber intake and take advantage of the many health benefits that grapes have to offer.
Additional Information
Grape juice is obtained from crushing and blending grapes into a liquid. In the wine industry, grape juice that contains 7–23 percent of pulp, skins, stems and seeds is often referred to as must. The sugars in grape juice allow it to be used as a sweetener, and fermented and made into wine, brandy, or vinegar.
In North America, the most common grape juice is purple and made from Concord grapes while white grape juice is commonly made from Niagara grapes, both of which are varieties of native American grapes, a different species from European wine grapes. In California, Sultana (known there as 'Thompson Seedless') grapes are sometimes diverted from the raisin or table market to produce white juice.
Grape juice can be made from all grape varieties after reaching appropriate maturity. Because of consumers' preferences for characteristics in colour, flavour and aroma, grape juice is primarily produced from American cultivars of Vitis labrusca.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2156 2024-05-20 15:19:10
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2158) Sugarcane juice
Details
Sugarcane juice is the liquid extracted from pressed sugarcane. It is consumed as a beverage in many places, especially where sugarcane is commercially grown, such as Southeast Asia, the Indian subcontinent, North Africa, mainly Egypt, and also in South America. Sugarcane juice is obtained by crushing peeled sugar cane in a mill and is one of the main precursors of rum.
In the United States where processed sugarcane syrup is used as a sweetener in food and beverage manufacturing, "evaporated cane juice" is considered by the Food and Drug Administration (FDA) to be a misleading term for "sugar" on product labels because the FDA regards "juice" as a liquid derived from fruits or vegetables; the preferred term is "cane sugar".
Health risks
There are some diseases that can be transmitted by raw sugar-cane, such as Leptospirosis. In Brazil, sugarcane juice has been linked to cases of Chagas disease, as sugarcane can contain traces of its responsible pathogen, Trypanosoma cruzi, left by infected bugs if not properly cleaned.
Drinking sugarcane juice in Egypt may pose health risks due to contamination with the mycotoxins, aflatoxin B1 and fumonisin B1.
Countries:
Brazil
Sugarcane juice, known locally as caldo de cana, is commonly sold by street vendors in Brazil. In a process similar to that of the street vendors of India, machines are used to press the sugarcane and the juice is extracted. It is sometimes served with lemon or pineapple juice.
Egypt
In Egypt, sugarcane juice is known as asab and is sold in juice shops around the country. The largest juice shop in Egypt is in Saft El Laban, Giza. Egyptians also mix lemon with asab and let it ferment to produce a fermented variant of the drink. The most highly prized asab comes from Minya, Egypt.
India
Sugarcane juice is sold by street vendors throughout India. The vendors put the sugarcane in a machine, which presses and extracts the sugarcane juice out. Sugarcane juice is usually served with a dash of lime and/or ginger juice. It is a very popular drink, especially during summer months, as a refreshing form of heat relief.
Before sugarcane was introduced to the southern region, it had already been cultivated for many centuries in Southeast Asia and India for its sweet juice, which was used to produce crude sugar. When Jesuit priests began growing sugarcane in what is now downtown New Orleans in 1751, they faced challenges in efficiently converting its juice into sugar due to the high costs, unreliability, and lack of profitability. However, by the 1790s, businessman Etienne de Bore, along with skilled sugar maker Antoine Morin from Santo Domingo, successfully refined sugarcane juice into granulated sugar, thereby achieving profitability in the process.
Indonesia
In Indonesia, sugarcane juice drink is called minuman sari tebu. The iced sugar cane juice is called es tebu. In Indonesian, tebu is sugarcane and es is ice. It is one of the traditional beverages commonly sold street-side in Indonesia. The sugarcane plant has been cultivated in Java since ancient times. The earliest record comes from a 9th-century inscription, dated from the Medang Mataram period, that describes a sweet drink called Nalaka Rasa, which translates as "sugarcane juice".
The juice is extracted using a pressing machine to squeeze the sugary sap from sugarcane. The machine might be human-powered, or powered by a gasoline engine or electricity. The juice sold there is always served cold with ice cubes. Traditionally, it is sold throughout the country, especially among street vendors that set their stall on the street side. Today, cleaner vendors work in food courts of malls and shopping centers.
Madagascar
In the eastern region of Madagascar, sugarcane juice is fermented to make an inexpensive alcoholic beverage called betsa-betsa. The drink is popular with locals because it is cheaper than beer.
Myanmar
In Myanmar, sugarcane juice is known as kyan ye and is available throughout the country. It is typically brewed during the summertime, and optionally blended with lime, jujube, or orange.
Pakistan
In 2019, the government of Pakistan declared sugarcane juice to be Pakistan's "national drink".
United States
In the United States, where the FDA regulates the description of ingredients on food labels, the term "sugarcane juice" cannot be used because it misleads consumers to believe that cane juice is similar to fruit or vegetable juices. Instead, the FDA recommends "cane sugar" or another term determined by manufacturers who should "review the final guidance and consider whether their labeling terminology accurately describes the basic nature and characterizing properties of the sweetener used".
Vietnam
Sugarcane juice, known as nước mía or mía đá, is common in Vietnam as a drink. Other fruit juices may be added to balance the sweetness, such as kumquat or chanh muối. It is sold at street stalls in plastic bags filled with ice or in disposable plastic cups.
Additional Information
Sugar originates from a grass called sugarcane. The cane stalks are harvested, mashed together, juiced, purified, cooled, and broken down into table sugar.
Sugarcane juice comes from the middle of the sugar-production process. Once the sugarcane is juiced and filtered, it cools to a syrupy texture. At that point, you can call it sugarcane juice. Sugarcane drinks contain sugarcane juice and water as their base. Add some flavor, such as ginger or lime, and you have a tasty beverage!
You can also use sugarcane juice in alcoholic beverages and can make your own sugarcane soda.
How Sugarcane Juice May Improve Your Health
Throughout time and around the world, people have thought that sugarcane juice is good for them. Traditionally, it's most often been residents of rural communities who believe that sugarcane juice:
* Promotes healthy urination and kidney health
* Can be used as a laxative
* Reduces inflammation
* Helps against overheating
* Acts as an antiseptic
* Protects against jaundice by helping the liver
* Is good as an all-around medicinal tonic.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2157 2024-05-21 13:20:37
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2159) Pomegranate Juice
Details
Pomegranate juice has become a popular drink, in large part due to much-trumpeted health claims. Pomegranates are the fruit of the Punica granatum tree. The fruit itself is bitter, so only the seeds are eaten. One pomegranate has nearly 30 milligrams (mg) of vitamin C, about 40% of the daily recommendation.
Pomegranate has been studied for its effects on lowering inflammation, improving heart health, and more. Research supports some health claims but has also found some safety concerns.
This article reviews research on pomegranate juice's uses, benefits, side effects, and interactions.
Dietary supplements are not regulated like drugs in the United States, meaning the Food and Drug Administration (FDA) does not approve them for safety and effectiveness before products are marketed. When possible, choose a supplement tested by a trusted third party, such as USP, ConsumerLabs, or NSF.
However, even if supplements are third-party tested, that doesn’t mean they are safe for all or effective in general. Therefore, it is important to talk to your healthcare provider about any supplements you plan to take and check in about potential interactions with other supplements or medications.
Supplement Facts
Active ingredient(s): α (alpha) and β (beta) punicalagin
Alternate name(s): Punica granatum L.
Legal status: Food, over-the-counter (OTC) herbal supplement (United States)
Suggested dose: 100 to 500 milliliters (mL) of juice
Safety considerations: Pregnant or breastfeeding people should ask their healthcare provider whether pomegranate juice is safe.
Uses of Pomegranate Juice
Supplement use should be individualized and vetted by a healthcare professional, such as a registered dietitian, pharmacist, or healthcare provider. No supplement is intended to treat, cure, or prevent disease.
Much of the research on pomegranate and pomegranate juice is preliminary. Studied conditions included:
Heart health
Inflammation
Infection
Dental plaque
Heart Health
A review of research says pomegranate juice may lower blood pressure and improve high blood pressure (hypertension) risk factors.
A recent randomized controlled trial similarly demonstrated that eight-week pomegranate juice consumption showed beneficial effects on blood pressure.
Other research suggested pomegranate juice had an impact on the following heart health indications:
Blood pressure
Low-density lipoprotein (LDL) ("bad") cholesterol
Triglyceride levels
Hypertension
Atherosclerosis (fatty plaque build-up in the insides of your arteries)
Coronary artery disease
Peripheral artery disease
It's important to note that most studies have not been done on humans, so it's challenging to say what benefits there are without further human studies. More research is needed to confirm pomegranate juice's benefits.
Inflammation
A review of studies suggests pomegranate may help fight chronic inflammation. It may have use in conditions like inflammatory bowel disease (IBD) and rheumatoid arthritis (RA).
A more recent meta-analysis and systematic review also revealed the potential of pomegranate products to fight inflammation.
However, more extensive and better-designed trials are needed.
Infection
Inflammation is part of the immune response to infection. Studies suggest pomegranate juice may help ward off infections. In one study, people undergoing dialysis had fewer hospitalizations for infections and fewer signs of inflammation. More research is needed to confirm these claims.
Dental Plaque
Limited evidence suggests pomegranate juice may help control dental plaque.
In a small study, 30 people used either a pomegranate dental rinse, an antiseptic dental rinse, or water. Researchers found the pomegranate solution performed just as well as the antiseptic solution. It had no adverse side effects.
It also appeared to inhibit the growth of germs that contribute to periodontitis (an inflammatory gum disease).
Other Uses
Research is ongoing into other health effects of pomegranate, including:
Cancer prevention
Chronic obstructive pulmonary disorder (COPD)
Diabetes
Erectile dysfunction
Kidney disease
More research is needed to determine whether pomegranate is safe and effective for these conditions.
What Are the Side Effects of Pomegranate Juice?
Pomegranate juice consumed in moderate amounts is most likely safe for most people. But certain people should exercise caution.
It's possible to be allergic to pomegranate, which can cause:
Itching
Swelling
Runny nose
Difficulty breathing
Anaphylaxis (a life-threatening reaction)
If you have oral allergy syndrome, you may be sensitive to pomegranate. This condition involves allergies to birch pollen and many fruits.
Some people have digestive side effects from pomegranate, such as diarrhea, which is the most common. Pomegranate root, stem, and peel contain substances that may be harmful in large amounts.
Pomegranate juice may also interact negatively with some medications.
Common Side Effects
Diarrhea is the most common side effect of pomegranate juice.
Severe Side Effects
Animal studies and human clinical trials have noted no severe side effects, including toxicity. However, pomegranate root, stem, and peel contain substances that may be harmful in large amounts.
Precautions
If you have oral allergy syndrome, you may be sensitive to pomegranate. This condition involves allergies to birch pollen and many fruits.
If you're pregnant or breastfeeding, ask your healthcare provider if pomegranate juice is safe.
Dosage: How Much Pomegranate Juice Should I Take?
Always speak with a healthcare provider before taking a supplement to ensure that the supplement and dosage are appropriate for your needs.
Pomegranate is available in many forms, including:
Pills
Tablets
Capsules
Softgels
Granules
Powder
Liquid
Paste
Labels often suggest a daily dose of eight ounces for adults. As a general rule, never take more than the recommended dose. Check with your child's pediatrician for suggestions on juice consumption for different age groups.
What Happens If I Take Too Much Pomegranate Juice?
Animal studies and human clinical trials have investigated the toxicity of pomegranate, and no adverse side effects have been noted. Pomegranate is safe at high doses in adults.22 However, this may be different for children.
Interactions
Some early evidence suggests combining pomegranate with statins (cholesterol-lowering drugs) is dangerous. Statins include but are not limited to the following:
Lipitor (atorvastatin)
Mevacor (lovastatin)
Zocor (simvastatin)
The combination of pomegranate and statins may cause rhabdomyolysis, a serious condition involving the breakdown of muscle fibers and possibly kidney failure. This may be due to pomegranates blocking an enzyme in the intestines, allowing you to absorb more medication. Grapefruit juice is better known for this effect, and many medication labels warn against drinking it.
Pomegranate juice may interact with other medications, such as:
Antiarrhythmics: Drugs for irregular heart rhythms, including Cordarone (amiodarone), Norpace (disopyramide), and quinidine
Anticoagulants: Drugs that affect blood coagulation, like Jantoven (warfarin)
Calcium channel blockers: Drugs that lower blood pressure, including Plendil (felodipine), Cardene (nicardipine), Procardia (nifedipine), Nimotop (nimodipine), and Sular (nisoldipine)
Immunosuppressants: Drugs for autoimmune disease, including Sandimmune (cyclosporine), Neoral (cyclosporine), and Prograf (tacrolimus)
Protease inhibitors: Anti-retroviral drugs, including Norvir (ritonavir)
It is essential to carefully read a supplement's ingredient list and nutrition facts panel to know which ingredients and how much of each ingredient is included. Review any supplement label with your healthcare provider to discuss potential interactions with foods, other supplements, and medications.
How to Store Pomegranate Juice
You'll find pomegranate juice at most grocery stores. It may be in the juice aisle or alongside whole fruit.
Organic juice may help you avoid harmful chemicals. Check the label to see if other juices or sweeteners are added.
Consider whether you want pasteurized juice. Pasteurization kills harmful bacteria, but it may also kill other compounds in the juice.
Some people choose to make their own fresh pomegranate juice. To do this, liquify pomegranate seeds in a blender. Then strain the juice to remove any unwanted roughage.
Similar Supplements
Grapefruit juice may have similar properties as pomegranate juice.
Grapefruit has been found to have antimicrobial, antiparasitic, insecticidal, antioxidant, and cardiovascular effects. Like pomegranate juice, it contains numerous bioactive compounds.
Similar Supplements
Grapefruit juice may have similar properties as pomegranate juice.
Grapefruit has been found to have antimicrobial, antiparasitic, insecticidal, antioxidant, and cardiovascular effects. Like pomegranate juice, it contains numerous bioactive compounds.
Additional Information
Pomegranate juice is made from the fruit of the pomegranate. It is used in cooking both as a fresh juice and as a concentrated syrup.
Research
Various primary studies have been conducted into possible health benefits derived from drinking pomegranate juice, but there is no good evidence to suggest any effect in blood pressure management, glucose and insulin management, or heart disease.
Potential risks
Drug interactions are possible.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2158 2024-05-22 16:35:38
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2160) Cucumber juice
Cucumber juice is the juice derived from cucumbers produced by squeezing or pressing it. Cucumbers are 98% water.
Cucumber juice is used in beverages such as math like the Bloody Mary, dishes such as cucumber soup, and in dips and salad dressings, such as green goddess dressing. Cucumber juice has significant amounts of potassium and is high in vitamin A. It also contains sterol and significant amounts of silicon.
Cucumber juice
Nutritional value per 1 ounce
Energy : 9 kcal (38 kJ)
Carbohydrates : 1 g
Vitamins : Quantity%DV
Vitamin C : 2%2 mg
Minerals : Quantity%DV†
Calcium : 3%40 mg
Iron : 1%.1 mg
Potassium : 1%41 mg
Sodium : 0%2 mg
Nutritional content source:
†Percentages estimated using US recommendations for adults, except for potassium, which is estimated based on expert recommendation from the National Academies.
Cucumber juice is used as an ingredient in cosmetics, soaps, shampoos, and lotions, and in eau de toilette and perfumes.
It was used in Russian traditional medicine to aid in the treatment of respiratory tract inflammation and to reduce lingering cough. In other traditions it was used to soothe heartburn and reduce acid in the stomach. For skin, it has been used to soothe burns and rashes. Cucumber juice has been described as a repellent against wood lice and fish-moths.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2159 2024-05-23 13:52:46
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2161) Carrot Juice
Carrot juice is juice produced from carrots.
Overview
Carrot juice has a particularly high content of β-carotene, a source of vitamin A, but it is also high in B complex vitamins like folate, and many minerals including calcium, copper, magnesium, potassium, phosphorus, and iron. A pound (454 g) of carrots will yield about a cup of juice (about 236 ml), which is a low yield compared to fruits like apples and oranges. However, carrot pulp is very tough; the main difficulty in juicing carrots is in separating the pulp from the juice.
Like many products high in beta-carotene, it may cause temporary carotenoderma, a benign skin condition resulting in an orange-yellow hue to the skin. Drinking more than 3 cups of carrot juice in a 24-hour period over a prolonged period of time may be enough to cause the condition.
Carrot juice has a uniquely sweet flavour of concentrated carrots. Unlike many juices, it is opaque. It is often consumed as a health drink. Carrots have been made into soups and juices for hundreds of years. In America carrot juice was one of the first colorants used to make cheese a darker color.
Nutritional information
100 g of canned carrot juice contains the following nutritional information according to the United States Department of Agriculture (USDA):
Calories : 40 kcal
Protein: 0.95 g
Fat: 0.15 g
Carbohydrates: 9.28 g
Dietary fibers: 0.8 g
Cholesterol: 0 mg (insignificant amount).

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2160 2024-05-24 14:01:11
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2162) Cost Insurance Freight
Gist
Cost, insurance, and freight (CIF) is an international shipping agreement, which represents the charges paid by a seller to cover the costs, insurance, and freight of a buyer's order while the cargo is in transit.
Details
What Is Cost, Insurance, and Freight (CIF)?
Cost, insurance, and freight (CIF) is an international shipping agreement, which represents the charges paid by a seller to cover the costs, insurance, and freight of a buyer's order while the cargo is in transit. Cost, insurance, and freight only applies to goods transported via a waterway, sea, or ocean.
The goods are exported to the buyer's port named in the sales contract. Once the goods are loaded onto the vessel, the risk of loss or damage is transferred from the seller to the buyer. However, insuring the cargo and paying for freight remains the seller's responsibility.
CIF is similar to carriage and insurance paid to (CIP), but CIF is used for only sea and waterway shipments, while CIP can be used for any mode of transport, such as by truck.
KEY TAKEAWAYS:
* Cost, insurance, and freight (CIF) is an international commerce term and only applies to goods shipped via a waterway or ocean.
* With cost, insurance, and freight, the seller covers the costs, insurance, and freight of a buyer's order while in transit.
* Once the cargo has been delivered to the buyer's destination port, the buyer assumes responsibility for the costs of importing and delivering the goods.
* However, the risk transfer occurs from the seller to the buyer when the goods have been loaded on the vessel.
* The buyer takes ownership of the goods once on the ship, and if the cargo is damaged during transit, the buyer must file a claim with the seller's insurance company.
Understanding Cost, Insurance, and Freight (CIF)
The contract terms of CIF define when the liability of the seller ends and the liability of the buyer begins. CIF is only used when shipping goods overseas or via a waterway.
The seller has the responsibility for paying the cost and freight of shipping the goods to the buyer's port of destination. Usually, exporters who have direct access to ships will use CIF. However, the buyer has responsibilities as well, which are outlined below.
Seller's Responsibilities
Under CIF terms, the seller's responsibilities include:
* Purchasing export licenses for the product
* Providing inspections of products
* Any charges or fees for shipping and loading the goods to the seller's port
* Packaging costs for exporting the cargo
* Fees for customs clearance, duty, and taxes (for exporting)
* Cost of shipping the freight via sea or waterway from the seller's port to the buyer's port of destination
* Cost of insuring the shipment up until the buyer's port of destination
* Covering the cost of any damage or destruction to the goods
The seller must deliver the goods to the ship within the agreed-upon timeframe and provide proof of delivery and loading.
Buyer's Responsibilities
Once the goods have arrived at the buyer's destination port, the buyer assumes responsibility for the costs associated with importing and delivering the goods. Some of these costs include the following:
* Unloading the product at the port terminal
* Transferring the product within the terminal and to the delivery site
* Custom duty charges and associated with importing the goods
* Charges for transporting, unloading, and delivering the goods to the final destination
Transfer of Risk
It's important to note that when shipping internationally, there can be different risk and cost transfer points between the buyer and seller, depending on the type of shipping agreement. Under CIF, the risk transfer is at a different point than the cost transfer. The exact details of the contract will determine when the liability for the goods transfers from seller to buyer.
Since the seller pays the shipping, freight, and insurance costs until the cargo arrives at the buyer's destination port, the cost transfer occurs when the goods have arrived at the buyer's port. However, the risk transfer occurs from the seller to the buyer when the goods have been loaded on the vessel. Although the seller must purchase insurance, the buyer has ownership of the goods once loaded onto the ship, and if the goods have been damaged during transit, the buyer must file a claim with the seller's insurance company.
Special Considerations
Since the buyer assumes the risk only when the cargo has been loaded on the vessel, certain situations may not be suitable for a CIF agreement. For example, with containerized cargo shipments, the goods may sit in a container for days before being loaded onto the vessel at the seller's port. Under CIF, the buyer would be at risk since the goods would not be insured while they sit in the container waiting to be loaded on the vessel. As a result, CIF agreements would not be appropriate for shipments, including containerized cargo.
Important : CIF is different from cost and freight provision (CFR) whereby sellers are not required to insure goods in transit.
Cost, Insurance, and Freight (CIF)
CIF is an international agreement between a buyer and seller in which the seller has responsibility for the cost, insurance, and freight of a sea or waterway shipment. Although the possession of the shipment transfers to the buyer once the goods have been loaded on the boat or ship, the seller is responsible for any shipping insurance and freight charges.
As a result, the seller is responsible for the costs of moving the shipment until the goods have arrived at the buyer's destination port. Some of these costs include fees for shipping, export customs clearance, duty, and taxes.
Once the goods have been delivered to the buyer's destination port, the buyer must pay the agreed price for the goods and is responsible for any import fees, taxes, or custom duty charges. Also, any transportation, inspection, and licensing costs as well as the cost to transport the goods to their final location are the buyer's responsibility.
Additional Information
Cost, insurance, and freight (CIF) is an international transportation agreement used when cargo is transported via waterway or sea. Under CIF, the seller is responsible for the shipping costs, insurance premiums, and freight of the buyer’s shipment. The full form of CIF is Cost, insurance, and freight.
Cost, Insurance, and Freight (CIF) is a common trade term or “Incoterm” that describes who pays for what and who is responsible for what when things are shipped from one country to another. CIF is mostly used for shipping by sea and is a deal between the exporter and the importer about different parts of the shipment. CIF can be further broken down as :
1. Cost (C): This indicates how much the thing itself costs. It’s how much you’re willing to pay for what you want.
2. Insurance (I): During the time the thing is being delivered to you, it could be damaged or lost. Through CIF, the buyer gets insurance that covers the item while it’s being shipped. Having insurance allows for reimbursement for items if they are destroyed in transit.
3. Freight (F): This is the cost for the seller to deliver the item to you. It’s the same as having to pay for handling and shipping. This shipping cost is taken care of by the seller.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2161 2024-05-24 23:19:22
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2163) Supersonic
Gist
It’s faster than the speed of sound, it’s supersonic! Seriously. Supersonic describes things that can travel faster than the speed of sound, like the passenger jet Concorde that used to zip from New York to London in under four hours.
Anything supersonic is so fast that you see it before you hear it. A high-speed fighter jet is supersonic, but there aren't any supersonic passenger planes since Concorde's retirement in 2003. Space shuttles and modern bullets are still supersonic. Originally, the word supersonic meant "having to do with sound waves beyond human hearing," but by 1934 it described movement exceeding the speed of sound, with ultrasonic taking on the old meaning. Sonic comes from the Latin sonus, or "sound."
Summary
Supersonic travel is a rate of travel of an object faster than the speed of sound (Mach 1). For objects travelling in the dry air of a temperature of 20 °C (68 °F) at sea level, this speed is approximately 343 m/s, 1,125 ft/s, 768 mph, 667 knots, or 1,235 km/h.
The term supersonic is used to describe a speed that is over the speed of sound (Mach 1). At a normal temperature like 70 degrees Fahrenheit (21.1 °C), the speed needed for something to be traveling at a faster than sound speed is about 344 m/s, 1,129 ft/s, 770 mph or 1,238 km/h. Speeds faster than 5 times the speed of sound are sometimes called hypersonic. Speeds where only some parts of the air around an object (like the propeller) reach supersonic speeds are called transonic (normally somewhere between Mach 0.8 and Mach 1.2).
Whips have operated supersonically for many centuries. Artillery became supersonic in the 19th century.
It can be very hard to reach supersonic speeds, because drag increases a lot near these speeds. This slows a plane, and for years made control difficult. These problems were called the "sound barrier". Jet engines and other developments solved the problems in the middle 20th century.
Details
Supersonic speed
Supersonic speed is the speed of an object that exceeds the speed of sound (Mach 1). For objects traveling in dry air of a temperature of 20 °C (68 °F) at sea level, this speed is approximately 343.2 m/s (1,126 ft/s; 768 mph; 667.1 kn; 1,236 km/h). Speeds greater than five times the speed of sound (Mach 5) are often referred to as hypersonic. Flights during which only some parts of the air surrounding an object, such as the ends of rotor blades, reach supersonic speeds are called transonic. This occurs typically somewhere between Mach 0.8 and Mach 1.2.
Sounds are traveling vibrations in the form of pressure waves in an elastic medium. Objects move at supersonic speed when the objects move faster than the speed at which sound propagates through the medium. In gases, sound travels longitudinally at different speeds, mostly depending on the molecular mass and temperature of the gas, and pressure has little effect. Since air temperature and composition varies significantly with altitude, the speed of sound, and Mach numbers for a steadily moving object may change. In water at room temperature supersonic speed can be considered as any speed greater than 1,440 m/s (4,724 ft/s). In solids, sound waves can be polarized longitudinally or transversely and have even higher velocities.
Supersonic fracture is crack motion faster than the speed of sound in a brittle material.
Early meaning
The word supersonic comes from two Latin derived words; 1) super: above and 2) sonus: sound, which together mean above sound, or faster than sound.
At the beginning of the 20th century, the term "supersonic" was used as an adjective to describe sound whose frequency is above the range of normal human hearing. The modern term for this meaning is "ultrasonic".
Supersonic objects
The tip of a bullwhip is thought to be the first object designed to break the sound barrier, resulting in the telltale "crack" (actually a small sonic boom). The wave motion travelling through the bullwhip is what makes it capable of achieving supersonic speeds. However, the first man-made supersonic boom was likely caused by a piece of cloth, spurring the whip's eventual development.
Most modern firearm bullets are supersonic, with rifle projectiles often travelling at speeds approaching and in some cases well exceeding Mach 3.
Most spacecraft are supersonic at least during portions of their reentry, though the effects on the spacecraft are reduced by low air densities. During ascent, launch vehicles generally avoid going supersonic below 30 km (~98,400 feet) to reduce air drag.
Note that the speed of sound decreases somewhat with altitude, due to lower temperatures found there (typically up to 25 km). At even higher altitudes the temperature starts increasing, with the corresponding increase in the speed of sound.
When an inflated balloon is burst, the torn pieces of latex contract at supersonic speed, which contributes to the sharp and loud popping noise.
Supersonic land vehicles
To date, only one land vehicle has officially travelled at supersonic speed, the ThrustSSC. The vehicle, driven by Andy Green, holds the world land speed record, having achieved an average speed on its bi-directional run of 1,228 km/h (763 mph) in the Black Rock Desert on 15 October 1997.
The Bloodhound LSR project planned an attempt on the record in 2020 at Hakskeenpan in South Africa with a combination jet and hybrid rocket propelled car. The aim was to break the existing record, then make further attempts during which [the members of] the team hope to reach speeds of up to 1,600 km/h (1,000 mph). The effort was originally run by Richard Noble who was the leader of the ThrustSSC project, however following funding issues in 2018, the team was bought by Ian Warhurst and renamed Bloodhound LSR. Later the project was indefinitely delayed due to the COVID-19 pandemic and the vehicle was put up for sale.
Supersonic flight
Most modern fighter aircraft are supersonic aircraft. No modern-day passenger aircraft are capable of supersonic speed, but there have been supersonic passenger aircraft, namely Concorde and the Tupolev Tu-144. Both of these passenger aircraft and some modern fighters are also capable of supercruise, a condition of sustained supersonic flight without the use of an afterburner. Due to its ability to supercruise for several hours and the relatively high frequency of flight over several decades, Concorde spent more time flying supersonically than all other aircraft combined by a considerable margin. Since Concorde's final retirement flight on November 26, 2003, there are no supersonic passenger aircraft left in service. Some large bombers, such as the Tupolev Tu-160 and Rockwell B-1 Lancer are also supersonic-capable.
The aerodynamics of supersonic aircraft is simpler than subsonic aerodynamics because the airsheets at different points along the plane often cannot affect each other. Supersonic jets and rocket vehicles require several times greater thrust to push through the extra aerodynamic drag experienced within the transonic region (around Mach 0.85–1.2). At these speeds aerospace engineers can gently guide air around the fuselage of the aircraft without producing new shock waves, but any change in cross area farther down the vehicle leads to shock waves along the body. Designers use the Supersonic area rule and the Whitcomb area rule to minimize sudden changes in size.
However, in practical applications, a supersonic aircraft must operate stably in both subsonic and supersonic profiles, hence aerodynamic design is more complex.
The main key to having low supersonic drag is to properly shape the overall aircraft to be long and thin, and close to a "perfect" shape, the von Karman ogive or Sears-Haack body. This has led to almost every supersonic cruising aircraft looking very similar to every other, with a very long and slender fuselage and large delta wings, cf. SR-71, Concorde, etc. Although not ideal for passenger aircraft, this shaping is quite adaptable for bomber use.
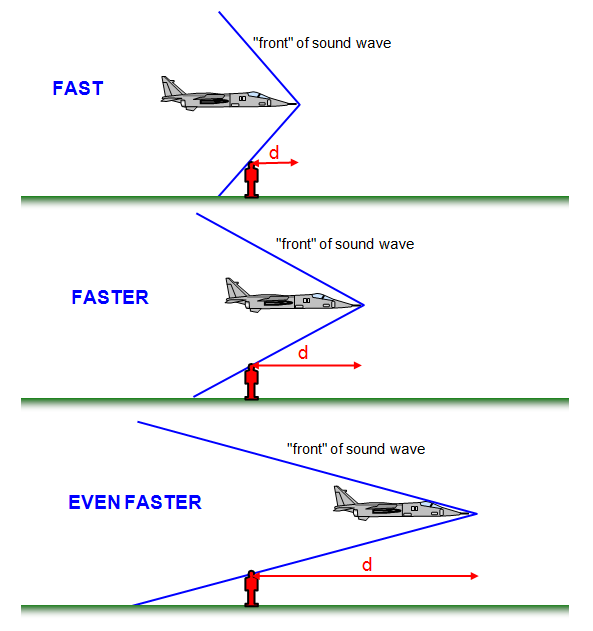
It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2162 2024-05-25 16:10:30
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2164) Free on Board
Gist
Free on Board (FOB) is a term used to indicate when the ownership of goods transfers from buyer to seller and who is liable for goods damaged or destroyed during shipping. "FOB Origin" means the buyer assumes all risk once the seller ships the product.
Summary
FOB stands for “free on board” or “freight on board” and is a designation that is used to indicate when liability and ownership of goods is transferred from a seller to a buyer.
Free on Board:
Free on board indicates whether the seller or the buyer is liable for goods that are damaged or destroyed during shipping. When used with an identified physical location, the designation determines which party has responsibility for the payment of the freight charges and at what point title for the shipment passes from the seller to the buyer.
In international shipping, for example, “FOB [name of originating port]” means that the seller (consignor) is responsible for transportation of the goods to the port of shipment and the cost of loading. The buyer (consignee) pays the costs of ocean freight, insurance, unloading, and transportation from the arrival port to the final destination. The seller passes the risk to the buyer when the goods are loaded at the originating port.
Freight on Board:
Freight on board is another term that is often used in place of free on board. However, it’s worth noting, this is not an official term.
How is “FOB” used in shipping documents?
The term “FOB” is used in four different ways when it comes to freight shipping. These include:
* FOB [place of origin], Freight Collect
* FOB [place of origin], Freight Prepaid
* FOB [place of destination], Freight Collect
* FOB [place of destination], Freight Prepaid
To understand each designation, we must first understand the difference between place of origin and place of destination and freight collect vs. freight prepaid. The first part of the designation determines where the buyer assumes title of the goods and the risk of damage from the seller (either at the moment the carrier picks the goods up for delivery or at the time of actual delivery). The second part indicates responsibility for freight charges. “Prepaid” means the seller has paid the freight; “collect” indicates the buyer is responsible for payment.
Place of Origin vs. Place of Destination:
Place of origin means the buyer assumes ownership of the shipment the moment the carrier picks up and signs the bill of lading while place of destination means the seller retains ownership and control of the goods until they are delivered. By denoting who “owns” the shipment, there is no ambiguity in responsibility of shipment.
Freight Collect vs. Freight Prepaid:
Freight collect means the person receiving the shipment is responsible for all freight charges. They also assume all risks and are responsible for filing claims in the case of loss or damage.
Freight prepaid is the opposite. The shipper accepts responsibility for all freight charges and risks.
Details
Free on Board (FOB) is a shipment term that defines the point in the supply chain when a buyer or seller becomes liable for the goods being transported. Purchase orders between buyers and sellers specify the FOB terms and help determine ownership, risk, and transportation costs.
"FOB Origin" or FOB Shipping Point" means the buyer accepts the title of the goods at the shipment point and assumes all risk once the seller ships the product. The buyer is responsible if the goods are damaged or lost while in transit.
"FOB Destination" means the seller retains the title of the goods and all responsibility during transit until the items reach the buyer.
KEY TAKEAWAYS
* Free on Board (FOB) is a term used to indicate when the ownership of goods transfers from buyer to seller and who is liable for goods damaged or destroyed during shipping.
* "FOB Origin" means the buyer assumes all risk once the seller ships the product.
* "FOB Destination" means the seller retains the risk of loss until the goods reach the buyer.
* FOB terms can impact inventory, shipping, and insurance costs.
Free on Board (FOB)
Understanding Free on Board (FOB)
FOB is a common term used for all types of shipping, both domestic and international. Shipping orders and contracts often describe the time and place of delivery, payment, when the risk of loss shifts from the seller to the buyer, and which party pays the costs of freight and insurance.
The vendor-client transaction defines the FOB terms in the purchase order. FOB status does not determine ownership, which is determined in the bill of sale or agreement between the buyer and seller, but defines which party takes responsibility for the shipment, whether at Origin, where the shipment begins or at Destination, where the shipment ends.
Each party should have a firm understanding of free on board (FOB) to ensure a smooth transfer of goods from the vendor to the client. Regardless of whether that transfer occurs on the domestic or international level, FOB terms can impact inventory, shipping, and insurance costs.
FOB Origin vs. FOB Destination
FOB origin, or shipping point, means that the buyer will receive the title for the goods they purchased when shipment begins. The seller’s responsibility ends when the items are placed with a shipment carrier, and the buyer must ensure their goods reach their final destination on time and undamaged.
For FOB destination, the seller retains ownership of the goods and is responsible for replacing damaged or lost items until the point where the goods have reached their final destination.
For shipments internationally, especially for companies ordering large inventory for global shipment on vessels and containers, international contracts establish and outline provisions, including the time and place of delivery, payment terms, and FOB designation to define when the risk of loss shifts from the seller to the buyer and which party pays for freight and insurance.
The most common international trade terms are Incoterms, which the International Chamber of Commerce (ICC) publishes, but firms that ship goods within the U.S. must adhere to the Uniform Commercial Code (UCC).
Since there is more than one set of rules, and legal definitions of FOB may differ from one country to another, the parties to a contract must indicate which governing laws are being used for a shipment.
FOB and Company Accounting
For FOB origin, after the goods are placed with a carrier for transport, the company records an increase in its inventory and the seller records the sale at the same time.
For FOB destination the seller completes the sale in its records once the goods arrive at their final destination and the buyer records the increase in its inventory at that time.
Other Shipping Terms
Although FOB Origin and Destination are the most familiar shipping terms, other terms include:
• FAS or Free Alongside: The seller must deliver goods on a ship that pulls up alongside a ship and close enough that the ship can use its lifting devices to bring the goods aboard.
• FCA or Free Carrier: The seller is obligated to deliver goods to an airport, shipping port, or railway terminal where the buyer has an established place of operation and takes delivery there.
• EXW or Ex Works: The seller prepares items for shipment from its location, but the buyer is responsible for picking the goods up and arranging shipment.
• DES or Delivered Ex Ship: The seller delivers products to a specified shipping port, where the buyer will take delivery on arrival.
What Is FOB Pricing?
The costs associated with FOB can include transportation of the goods to the port of shipment, loading the goods onto the shipping vessel, freight transport, insurance, and unloading and transporting the goods from the arrival port to the final destination.
Who Pays Freight for FOB Origin?
If the terms include the phrase "FOB origin, freight collect," the buyer is responsible for freight charges. If the terms include "FOB origin, freight prepaid," the buyer assumes the responsibility for goods at the point of origin, but the seller pays the cost of shipping.
What Is the Difference Between FOB and CIF?
CIF (Cost, Insurance, and Freight) and FOB (Free on Board) are two widely used INCOTERM agreements.
Although the definition of both terms can differ across countries and is ultimately determined by each vendor-client contract, historically, FOB transfers liability from seller to buyer when the shipment reaches the port or other facility designated as the point of origin. With a CIF agreement, the seller pays costs and assumes liability until the goods reach the port of destination chosen by the buyer.
The Bottom Line
Free on Board (FOB) is a shipment term that defines the point in the supply chain when a buyer or seller assumes responsibility for the goods being transported. FOB terms like FOB Origin and FOB Destination help define ownership, risk, and transportation costs for both buyers and sellers.
Additional Information
FOB (free on board) is a term in international commercial law specifying at what point respective obligations, costs, and risk involved in the delivery of goods shift from the seller to the buyer under the Incoterms standard published by the International Chamber of Commerce. FOB is only used in non-containerized sea freight or inland waterway transport. As with all Incoterms, FOB does not define the point at which ownership of the goods is transferred.
The term FOB is also used in modern domestic shipping within North America to describe the point at which a seller is no longer responsible for shipping costs.
Ownership of a cargo is independent of Incoterms, which relate to delivery and risk. In international trade, ownership of the cargo is defined by the contract of sale and the bill of lading or waybill.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2163 2024-05-26 15:07:59
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2165) Tensile Strength
Gist
Tensile strength can be defined as the maximum stress that a material can bear before breaking when it is allowed to be stretched or pulled.
Summary
Tensile strength, maximum load that a material can support without fracture when being stretched, divided by the original cross-sectional area of the material. Tensile strengths have dimensions of force per unit area and in the English system of measurement are commonly expressed in units of pounds per square inch, often abbreviated to psi. When stresses less than the tensile strength are removed, a material returns either completely or partially to its original shape and size. As the stress reaches the value of the tensile strength, however, a material, if ductile, that has already begun to flow plastically rapidly forms a constricted region called a neck, where it then fractures.
Details
Tensile strength is the maximum amount of tensile stress a material can withstand before it fails or breaks. It is a measure of the material's ability to resist deformation under tension or stretching forces.
When high tensile loads are applied, ductile and brittle materials will approach failure. This process begins with a uniform deformation throughout the sample followed by an increase in length and a decrease in width at the same rate.
Tensile strength is an important property of materials used in engineering and manufacturing applications. It is a critical factor in designing structures, such as buildings, bridges and aircraft, that can withstand forces due to tension or stretching. It is also important in the design of products that are subject to pulling or stretching forces, such as ropes, cables and wires.
Tensile strength is usually determined by conducting a tensile test, which involves applying an axial load to a test specimen until it fractures. The load is applied using a tensile testing machine, which measures the amount of force required to break the specimen. The maximum load the specimen can withstand before it fractures is the tensile strength.
Tensile strength is usually reported in units of force per unit area, such as pounds per square inch (psi) or megapascals (MPa). The tensile strength of a material depends on its composition, structure and processing history. For example, steel with a higher carbon content tends to have a higher tensile strength than steel with a lower carbon content.
A material's tensile strength is an important factor in determining its suitability for a particular application. For example, in the aerospace industry, the tensile strength of materials used in aircraft structures is critical to ensure the safety and reliability of the aircraft. Similarly, in the construction industry, the tensile strength of materials used in building structures, such as steel and concrete, is critical to ensure the structures can withstand the forces of wind, earthquakes and other environmental factors.
Tensile strength can also be affected by various factors, such as temperature, strain rate and fatigue. For example, the tensile strength of some materials may decrease at high temperatures, while others may exhibit an increase in strength. Similarly, the tensile strength of a material may decrease as the rate of deformation increases. Fatigue can also affect the tensile strength of a material, causing it to decrease over time under repeated loading.
Ultimate tensile strength an intensive property, meaning it depends on the sample size, which measures the amount of stress a material can withstand before it moves from experiencing uniform plastic deformation to experiencing local concentrated deformation. Necking starts at this point.
Because necking can cause failure and may be life-threatening, it is important to consider this parameter while selecting suitable materials for an application.
Designing for ultimate tensile strength means part of the asset will permanently deform once it's subjected to the load for which it was designed. This deformation may cause the material’s crystal structure to change, making it no longer able to function.
In case of cold-drawn steel bars, the tensile strength is increased by cold drawing where the bar is drawn through a die reducing its outer diameter. It is critical for shafts used in various applications.
Additional Information
Tensile strength is a measurement of the force required to pull something such as rope, wire, or a structural beam to the point where it breaks.
The tensile strength of a material is the maximum amount of tensile stress that it can take before failure, for example breaking.
There are three typical definitions of tensile strength:
* Yield strength - The stress a material can withstand without permanent deformation. This is not a sharply defined point. Yield strength is the stress which will cause a permanent deformation of 0.2% of the original dimension.
* Ultimate strength - The maximum stress a material can withstand.
* Breaking strength - The stress coordinate on the stress-strain curve at the point of rupture.
It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2164 2024-05-27 14:29:20
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2166) Virtual Private Network
Gist
A VPN, which stands for virtual private network, establishes a digital connection between your computer and a remote server owned by a VPN provider, creating a point-to-point tunnel that encrypts your personal data, masks your IP address, and lets you sidestep website blocks and firewalls on the internet.
Summary
A VPN (virtual private network) is a service that creates a safe, encrypted online connection. Internet users may use a VPN to give themselves more privacy and anonymity online or circumvent geographic-based blocking and censorship. VPNs essentially extend a private network across a public network, which should allow a user to securely send and receive data across the internet.
Typically, a VPN is used over a less secure network, such as the public internet. Internet service providers (ISPs) normally have a rather large amount of insight into a customer's activities. In addition, some unsecured Wi-Fi access points (APs) may be a convenient avenue for attackers to gain access to a user's personal data. An internet user could use a VPN to avoid these encroachments on privacy.
VPNs can be used to hide a user's browser history, Internet Protocol (IP) address and geographical location, web activity or devices being used. Anyone on the same network will not be able to see what a VPN user is doing. This makes VPNs a go-to tool for online privacy.
A VPN uses tunneling protocols to encrypt data at the sending end and decrypts it at the receiving end. The originating and receiving network addresses are also encrypted to provide better security for online activities.
VPN apps are often used to protect data transmissions on mobile devices. They can also be used to visit websites that are restricted by location. Secure access through a mobile VPN should not be confused with private browsing, however. Private browsing does not involve encryption; it is simply an optional browser setting that prevents identifiable user data from being collected.
Details
VPN is a mechanism of employing encryption, authentication, and integrity protection so that we can use a public network as if it is a private network. It offers a high amount of security and allows users to remotely access private networks. In this article, we will cover every point about virtual private networks.
What is a VPN?
A virtual private network (VPN) is a technology that creates a safe and encrypted connection over a less secure network, such as the Internet. A Virtual Private Network is a way to extend a private network using a public network such as the Internet. The name only suggests that it is a “Virtual Private Network”, i.e. user can be part of a local network sitting at a remote location. It makes use of tuneling protocols to establish a secure connection.
Virtual Private Network
History of VPNs
ARPANET introduced the idea of connecting distant computers in the 1960s. The foundation for current internet connectivity was established by ensuring the development of protocols like TCP/IP in the 1980s. Particular VPN technologies first appeared in the 1990s in response to the growing concerns about online privacy and security.
How Does a VPN Work?
Let us understand VPN with an example think of a situation where the corporate office of a bank is situated in Washington, USA. This office has a local network consisting of say 100 computers. Suppose other branches of the bank are in Mumbai, India, and Tokyo, Japan. The traditional method of establishing a secure connection between the head office and the branch was to have a leased line between the branches and head office which was a very costly as well as troublesome job. VPN lets us effectively overcome this issue.
The situation is described below
* All 100 hundred computers of the corporate office in Washington are connected to the VPN server(which is a well-configured server containing a public IP address and a switch to connect all computers present in the local network i.e. in the US head office).
* The person sitting in the Mumbai office connects to The VPN server using a dial-up window and the VPN server returns an IP address that belongs to the series of IP addresses belonging to a local network of the corporate office.
* Thus person from the Mumbai branch becomes local to the head office and information can be shared securely over the public internet.
* So this is the intuitive way of extending the local network even across the geographical borders of the country.
VPN is well Exploited all Across the Globe
We will explain to you with an example. Suppose we are using smartphones regularly. Spotify Swedish music app that is not active in India But we are making full use of it sitting in India. So how ?? VPN can be used to camouflage our geolocation.
* Suppose the IP address is 101.22.23.3 which belongs to India. That’s why our device is not able to access the Spotify music app.
* But the magic began when we used the Psiphon app which is an Android app used to change the device IP address to the IP address of the location we want(say US where Spotify works seamlessly).
* The IP address is changed using VPN technology. Basically what happens is that your device will connect to a VPN server of the respective country that you have entered in your location textbox of the Psiphon app and now you will inherit a new IP from this server.
Now we typed “What is my IP address”? Amazingly the IP address changed to 45.79.66.125 which belongs to the USA And since Spotify works well in the US, we can use it now being in India (virtually in the USA). Is not that good? obviously, it is very useful.
* VPN also ensures security by providing an encrypted tunnel between the client and the VPN server.
* VPN is used to bypass many blocked sites.
* VPN facilitates Anonymous browsing by hiding your IP address.
* Also, the most appropriate Search engine optimization (SEO) is done by analyzing the data from VPN providers which provide country-wise statics of browsing a particular product.
* VPNs encrypt your internet traffic, safeguarding your online activities from potential eavesdropping and cyber threats, thereby enhancing your privacy and data protection.
Types of VPN
There are several types of VPN and these are vary from specific requirement in computer network. Some of the VPN are as follows:
* Remote Access VPN
* Site to Site VPN
* Cloud VPN
* Mobile VPN
* SSL VPN.
Additional Information
A virtual private network (VPN) is a mechanism for creating a secure connection between a computing device and a computer network, or between two networks, using an insecure communication medium such as the public Internet.
A VPN can extend access to a private network (one that disallows or restricts public access) to users who do not have direct access to it, such as an office network allowing secure access from off-site over the Internet.
The benefits of a VPN include security, reduced costs for dedicated communication lines, and greater flexibility for remote workers.
A VPN is created by establishing a virtual point-to-point connection through the use of tunneling protocols over existing networks. A VPN available from the public Internet can provide some of the benefits[example needed] of a private wide area network (WAN).
It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2165 2024-05-28 14:56:05
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2167) File Transfer Protocol
Gist
FTP (File Transfer Protocol) is a standard network protocol used for the transfer of files from one host to another over a TCP-based network, such as the Internet. FTP works by opening two connections that link the computers trying to communicate with each other.
Summary
FTP (File Transfer Protocol) is a standard network protocol used for the transfer of files from one host to another over a TCP-based network, such as the Internet.
FTP works by opening two connections that link the computers trying to communicate with each other. One connection is designated for the commands and replies that get sent between the two clients, and the other channel handles the transfer of data. During an FTP transmission, there are four commands used by the computers, servers, or proxy servers that are communicating. These are “send,” “get,” “change directory,” and “transfer.”
While transferring files, FTP uses three different modes: block, stream, and compressed. The stream mode enables FTP to manage information in a string of data without any boundaries between them. The block mode separates the data into blocks, and in the compress mode, FTP uses an algorithm called the Lempel-Ziv to compress the data.
What is FTP useful for?
One of the main reasons why modern businesses and individuals need FTP is its ability to perform large file size transfers. When sending a relatively small file, like a Word document, most methods will do, but with FTP, you can send hundreds of gigabytes at once and still get a smooth transmission.
The ability to send larger amounts of data, in turn, improves workflow. Because FTP allows you to send multiple files at once, you can select several and then send them all at the same time. Without FTP services, you may have to send them one by one, when you could be accomplishing other work.
For example, if you have to transfer a large collection of important documents from headquarters to a satellite office but have a meeting to attend in five minutes, you can use FTP to send them all at once. Even if it takes 15 minutes for the transfer to complete, FTP can handle it, freeing you up to attend the meeting.
Details
FTP (File Transfer Protocol) is a network protocol for transmitting files between computers over Transmission Control Protocol/Internet Protocol (TCP/IP) connections. Within the TCP/IP suite, FTP is considered an application layer protocol.
In an FTP transaction, the end user's computer is typically called the local host. The second computer involved in FTP is a remote host, which is usually a server. Both computers need to be connected via a network and configured properly to transfer files via FTP. Servers must be set up to run FTP services, and the client must have FTP software installed to access these services.
Although many file transfers can be conducted using Hypertext Transfer Protocol (HTTP) -- another protocol in the TCP/IP suite -- FTP is still commonly used to transfer files behind the scenes for other applications, such as banking services. It is also sometimes used to download new applications via web browsers.
How does FTP work?
FTP is a client-server protocol that relies on two communications channels between the client and server: a command channel for controlling the conversation and a data channel for transmitting file content.
Here is how a typical FTP transfer works:
* A user typically needs to log on to the FTP server, although some servers make some or all of their content available without a login, a model known as anonymous FTP.
* The client initiates a conversation with the server when the user requests to download a file.
Using FTP, a client can upload, download, delete, rename, move and copy files on a server.
FTP sessions work in active or passive modes:
* Active mode. After a client initiates a session via a command channel request, the server creates a data connection back to the client and begins transferring data.
* Passive mode. The server uses the command channel to send the client the information it needs to open a data channel. Because passive mode has the client initiating all connections, it works well across firewalls and network address translation gateways.
Active FTP and passive FTP compared
Users can work with FTP via a simple command-line interface -- from a console or terminal window in Microsoft Windows, Apple macOS or Linux -- or with a dedicated graphical user interface. Web browsers can also serve as FTP clients.
Why is FTP important and what is it used for?
FTP is a standard network protocol that can enable expansive file transfer capabilities across IP networks. Without FTP, file and data transfer can be managed with other mechanisms -- such as email or an HTTP web service -- but those other options lack the clarity of focus, precision and control that FTP enables.
FTP is used for file transfers between one system and another, and it has several common use cases, including the following:
1. Backup. FTP can be used by backup services or individual users to backup data from one location to a secured backup server running FTP services.
2. Replication. Similar to backup, replication involves duplication of data from one system to another but takes a more comprehensive approach to provide higher availability and resilience. FTP can also be used to facilitate this.
3. Access and data loading. FTP is also commonly used to access shared web hosting and cloud services as a mechanism to load data onto a remote system.
FTP types
There are several different ways an FTP server and client software can conduct a file transfer using FTP:
* Anonymous FTP. This is the most basic form of FTP. It provides support for data transfers without encrypting data or using a username and password. It's most commonly used for download of material that is allowed for unrestricted distribution. It works on port
* Password-protected FTP. This is also a basic FTP service, but it requires the use of a username and password, though the service might not be encrypted or secure. It also works on port 21.
* FTP Secure (FTPS). Sometimes referred to as FTP Secure Sockets Layer (FTP-SSL), this approach enables implicit Transport Layer Security (TLS) as soon as an FTP connection is established. FTPS was initially used to help enable a more secure form of FTP data transfer. It typically defaults to using port 990.
* FTP over explicit SSL/TLS (FTPES). This approach enables explicit TLS support by upgrading an FTP connection over port 21 to an encrypted connection. This is a commonly used approach by web and file sharing services to enable secure file transfers.
* Secure FTP (SFTP). This is technically not an FTP protocol, but it functions similarly. Rather, SFTP is a subset of the Secure Shell (SSH) protocol that runs over port 22. SSH is commonly used by systems administrators to remotely and securely access systems and applications, and SFTP provides a mechanism within SSH for secure file transfer.
FTP security
FTP was initially defined in 1971, predating TCP and IP, and it has been redefined several times since then to accommodate new technologies, including the use of TCP/IP, or Request for Comments 765 and RFC 959, and IPv6, or RFC 2428.
FTP has also undergone several updates to enhance FTP security. These include versions that encrypt via an implicit TLS connection (FTPS) or explicit TLS connection (FTPES) or that work with SFTP.
By default, FTP does not encrypt traffic, and individuals can capture packets to read usernames, passwords and other data. By encrypting FTP with FTPS or FTPES, data is protected, limiting the ability of an attacker to eavesdrop on a connection and steal data.
FTP may still be vulnerable to brute-force attacks against user/password authentication spoofing, an FTP bounce attack or a distributed denial-of-service attack.
History of FTP
The first specification for FTP was published as RFC 114 on April 16, 1971, and was written by Abhay Bhushan, then a student at the Massachusetts Institute of Technology. The original idea behind FTP was to enable the transfer of files over ARPANET, the precursor to the internet.
As the modern internet began to take shape, the FTP specification underwent several revisions to align with networking standards, including TCP/IP. In 1980, a new version of FTP was defined in RFC 765 by Jon Postel, a research scientist at the Information Sciences Institute at the University of Southern California at the time. Five years later, FTP was redefined yet again with RFC 959, which introduced new management capabilities for the protocol, including the ability to make and remove a file directory. Prior iterations of FTP were largely limited to transferring files to and from existing file directory structures.
In 1997, RFC 959 was updated with new capabilities defined in RFC 2228 to provide security capabilities. Two years later, FTP was updated with RFC 2428 to support the IPv6 protocol.
Additional Information
The File Transfer Protocol (FTP) is a standard communication protocol used for the transfer of computer files from a server to a client on a computer network. FTP is built on a client–server model architecture using separate control and data connections between the client and the server. FTP users may authenticate themselves with a plain-text sign-in protocol, normally in the form of a username and password, but can connect anonymously if the server is configured to allow it. For secure transmission that protects the username and password, and encrypts the content, FTP is often secured with SSL/TLS (FTPS) or replaced with SSH File Transfer Protocol (SFTP).
The first FTP client applications were command-line programs developed before operating systems had graphical user interfaces, and are still shipped with most Windows, Unix, and Linux operating systems. Many dedicated FTP clients and automation utilities have since been developed for desktops, servers, mobile devices, and hardware, and FTP has been incorporated into productivity applications such as HTML editors and file managers.
An FTP client used to be commonly integrated in web browsers, where file servers are browsed with the URI prefix "ftp://". In 2021, FTP support was dropped by Google Chrome and Firefox, two major web browser vendors, due to it being superseded by the more secure SFTP and FTPS; although neither of them have implemented the newer protocols.
It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2166 2024-05-29 14:31:54
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2168) Hyper Text Transfer Protocol Secure
Gist
Hypertext transfer protocol secure (HTTPS) is the secure version of HTTP, which is the primary protocol used to send data between a web browser and a website. HTTPS is encrypted in order to increase security of data transfer. This is particularly important when users transmit sensitive data, such as by logging into a bank account, email service, or health insurance provider.
Any website, especially those that require login credentials, should use HTTPS. In modern web browsers such as Chrome, websites that do not use HTTPS are marked differently than those that are. Look for a padlock in the URL bar to signify the webpage is secure. Web browsers take HTTPS seriously; Google Chrome and other browsers flag all non-HTTPS websites as not secure.
Summary
Hypertext Transfer Protocol Secure (HTTPS) is a protocol that secures communication and data transfer between a user's web browser and a website. HTTPS is the secure version of HTTP.
The protocol protects users against eavesdroppers and man-in-the-middle (MitM) attacks. It also protects legitimate domains from domain name system (DNS) spoofing attacks.
HTTPS plays a significant role in securing websites that handle or transfer sensitive data, including data handled by online banking services, email providers, online retailers, healthcare providers and more. Simply put, any website that requires login credentials or involves financial transactions should use HTTPS to ensure the security of users, transactions and data.
HTTP vs. HTTPS
A malicious actor can easily impersonate, modify or monitor an HTTP connection. HTTPS provides protection against these vulnerabilities by encrypting all exchanges between a web browser and web server. As a result, HTTPS ensures that no one can tamper with these transactions, thus securing users' privacy and preventing sensitive information from falling into the wrong hands.
HTTPS is not a separate protocol from HTTP. Rather, it is a variant that uses Transport Layer Security (TLS)/Secure Sockets Layer (SSL) encryption over HTTP to secure communications. When a web server and web browser talk to each other over HTTPS, they engage in what's known as a handshake -- an exchange of TLS/SSL certificates -- to verify the provider's identity and protect the user and their data.
An HTTPS URL begins with https:// instead of http://. Most web browsers show that a website is secure by displaying a closed padlock symbol to the left of the URL in the browser's address bar. In some browsers, users can click on the padlock icon to check if an HTTPS-enabled website's digital certificate includes identifying information about the website owner, such as their name or company name.
Details
Protocol (HTTP). It uses encryption for secure communication over a computer network, and is widely used on the Internet. In HTTPS, the communication protocol is encrypted using Transport Layer Security (TLS) or, formerly, Secure Sockets Layer (SSL). The protocol is therefore also referred to as HTTP over TLS, or HTTP over SSL.
The principal motivations for HTTPS are authentication of the accessed website and protection of the privacy and integrity of the exchanged data while it is in transit. It protects against man-in-the-middle attacks, and the bidirectional block cipher encryption of communications between a client and server protects the communications against eavesdropping and tampering. The authentication aspect of HTTPS requires a trusted third party to sign server-side digital certificates. This was historically an expensive operation, which meant fully authenticated HTTPS connections were usually found only on secured payment transaction services and other secured corporate information systems on the World Wide Web. In 2016, a campaign by the Electronic Frontier Foundation with the support of web browser developers led to the protocol becoming more prevalent. HTTPS is now used more often by web users than the original, non-secure HTTP, primarily to protect page authenticity on all types of websites, secure accounts, and keep user communications, identity, and web browsing private.
Overview
The Uniform Resource Identifier (URI) scheme HTTPS has identical usage syntax to the HTTP scheme. However, HTTPS signals the browser to use an added encryption layer of SSL/TLS to protect the traffic. SSL/TLS is especially suited for HTTP, since it can provide some protection even if only one side of the communication is authenticated. This is the case with HTTP transactions over the Internet, where typically only the server is authenticated (by the client examining the server's certificate).
HTTPS creates a secure channel over an insecure network. This ensures reasonable protection from eavesdroppers and man-in-the-middle attacks, provided that adequate cipher suites are used and that the server certificate is verified and trusted.
Because HTTPS piggybacks HTTP entirely on top of TLS, the entirety of the underlying HTTP protocol can be encrypted. This includes the request's URL, query parameters, headers, and cookies (which often contain identifying information about the user). However, because website addresses and port numbers are necessarily part of the underlying TCP/IP protocols, HTTPS cannot protect their disclosure. In practice this means that even on a correctly configured web server, eavesdroppers can infer the IP address and port number of the web server, and sometimes even the domain name (e.g. www.example.org, but not the rest of the URL) that a user is communicating with, along with the amount of data transferred and the duration of the communication, though not the content of the communication.
Web browsers know how to trust HTTPS websites based on certificate authorities that come pre-installed in their software. Certificate authorities are in this way being trusted by web browser creators to provide valid certificates. Therefore, a user should trust an HTTPS connection to a website if and only if all of the following are true:
* The user trusts that their device, hosting the browser and the method to get the browser itself, is not compromised (i.e. there is no supply chain attack).
* The user trusts that the browser software correctly implements HTTPS with correctly pre-installed certificate authorities.
* The user trusts the certificate authority to vouch only for legitimate websites (i.e. the certificate authority is not compromised and there is no mis-issuance of certificates).
* The website provides a valid certificate, which means it was signed by a trusted authority.
* The certificate correctly identifies the website (e.g., when the browser visits "https://example.com", the received certificate is properly for "example.com" and not some other entity).
* The user trusts that the protocol's encryption layer (SSL/TLS) is sufficiently secure against eavesdroppers.
HTTPS is especially important over insecure networks and networks that may be subject to tampering. Insecure networks, such as public Wi-Fi access points, allow anyone on the same local network to packet-sniff and discover sensitive information not protected by HTTPS. Additionally, some free-to-use and paid WLAN networks have been observed tampering with webpages by engaging in packet injection in order to serve their own ads on other websites. This practice can be exploited maliciously in many ways, such as by injecting malware onto webpages and stealing users' private information.
HTTPS is also important for connections over the Tor network, as malicious Tor nodes could otherwise damage or alter the contents passing through them in an insecure fashion and inject malware into the connection. This is one reason why the Electronic Frontier Foundation and the Tor Project started the development of HTTPS Everywhere, which is included in Tor Browser.
As more information is revealed about global mass surveillance and criminals stealing personal information, the use of HTTPS security on all websites is becoming increasingly important regardless of the type of Internet connection being used. Even though metadata about individual pages that a user visits might not be considered sensitive, when aggregated it can reveal a lot about the user and compromise the user's privacy.
Deploying HTTPS also allows the use of HTTP/2 and HTTP/3 (and their predecessors SPDY and QUIC), which are new HTTP versions designed to reduce page load times, size, and latency.
It is recommended to use HTTP Strict Transport Security (HSTS) with HTTPS to protect users from man-in-the-middle attacks, especially SSL stripping.
HTTPS should not be confused with the seldom-used Secure HTTP (S-HTTP) specified in RFC 2660.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2167 2024-05-30 14:27:44
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2169) Information Technology
Gist
Information technology (IT) is a set of related fields that encompass computer systems, software, programming languages, and data and information processing, and storage. IT forms part of information and communications technology (ICT).
Summary
Information technology (IT) is a set of related fields that encompass computer systems, software, programming languages, and data and information processing, and storage. IT forms part of information and communications technology (ICT). An information technology system (IT system) is generally an information system, a communications system, or, more specifically speaking, a computer system — including all hardware, software, and peripheral equipment — operated by a limited group of IT users, and an IT project usually refers to the commissioning and implementation of an IT system. IT systems play a vital role in facilitating efficient data management, enhancing communication networks, and supporting organizational processes across various industries. Successful IT projects require meticulous planning, seamless integration, and ongoing maintenance to ensure optimal functionality and alignment with organizational objectives.
Although humans have been storing, retrieving, manipulating, and communicating information since the earliest writing systems were developed, the term information technology in its modern sense first appeared in a 1958 article published in the Harvard Business Review; authors Harold J. Leavitt and Thomas L. Whisler commented that "the new technology does not yet have a single established name. We shall call it information technology (IT)." Their definition consists of three categories: techniques for processing, the application of statistical and mathematical methods to decision-making, and the simulation of higher-order thinking through computer programs.
The term is commonly used as a synonym for computers and computer networks, but it also encompasses other information distribution technologies such as television and telephones. Several products or services within an economy are associated with information technology, including computer hardware, software, electronics, semiconductors, internet, telecom equipment, and e-commerce.
Based on the storage and processing technologies employed, it is possible to distinguish four distinct phases of IT development: pre-mechanical (3000 BC — 1450 AD), mechanical (1450 — 1840), electromechanical (1840 — 1940), and electronic (1940 to present).
Information technology is also a branch of computer science, which can be defined as the overall study of procedure, structure, and the processing of various types of data. As this field continues to evolve across the world, its overall priority and importance has also grown, which is where we begin to see the introduction of computer science-related courses in K-12 education.
Details
Information technology (IT) is the use of computers, storage, networking and other physical devices, infrastructure and processes to create, process, store, secure and exchange all forms of electronic data. Typically, IT is used in the context of business operations, as opposed to the technology used for personal or entertainment purposes. The commercial use of IT encompasses both computer technology and telecommunications.
Harvard Business Review coined the term information technology in 1958 to distinguish between purpose-built machines designed to perform a limited scope of functions and general-purpose computing machines that could be programmed for various tasks. As the IT industry evolved from the mid-20th century, computing capability increased, while device cost and energy consumption decreased, a cycle that continues today when new technologies emerge.
Types of information technology
Information technology encompasses a wide range of technologies and systems that are used to store, retrieve, process and transmit data for specific use cases.
Common information technology types include the following:
* Internet and web technologies. This includes the tools and protocols used to access, navigate and interact with information on the internet. Examples include web browsers, websites, web servers, Hypertext Markup Language, cascading style sheets, JavaScript, HTTP and other internet-related technologies.
* Cloud computing. This involves the delivery of computing resources and services over the internet on a pay-per-use basis. This can include infrastructure as a service, platform as a service, software as a service and cloud storage options.
* Databases. This includes IT systems and software used to store, organize and retrieve data. Examples include MySQL, NoSQL, relational database management systems and MongoDB.
* Artificial intelligence and machine learning. AI and ML-based IT technologies use algorithms and statistical models to enable computers to perform tasks that typically require human intelligence. Examples include speech recognition, image recognition and natural language processing.
* Cybersecurity. This type of IT includes technologies and best practices designed to protect IT systems, networks and data from unauthorized access, cyber attacks and other security threats. Cybersecurity can be enforced through firewalls, antivirus software, encryption, intrusion detection systems and security policies.
* Internet of things. This includes the network of interconnected devices and sensors that collect, exchange and analyze data. IoT technologies enable the integration of physical objects into computer systems, providing automation, monitoring and control in various domains.
* IT governance. This involves making policies and rules for the organization to ensure effective operation.
Data analytics and business intelligence. BI focuses on tools and techniques for extracting insights from large data sets to support decision-making and business operations. This can include data mining, statistical analysis, data visualization and predictive modeling.
What does information technology encompass?
The IT department ensures that the organization's systems, networks, applications, data and information all connect and function properly. The IT team handles the following three major areas:
Deploying and maintaining business applications, services and infrastructure -- including servers, networks and storage.
Monitoring, optimizing and troubleshooting the performance of applications, services and infrastructure.
Overseeing the security and governance of applications, services and infrastructure.
Most IT staff have different responsibilities within the team that can be broken into the following key areas:
Administration. Administrators handle the day-to-day deployment, operation and monitoring of an IT environment, including systems, networks and applications. Admins often perform a range of other duties such as software upgrades, user training, software license management, procurement, security, data management and observing adherence to business process and compliance requirements. Effective delegation is also part of IT administration and is crucial for a team's productivity.
Support. Help desk staff specialize in answering questions, gathering information and directing troubleshooting efforts for hardware and software. IT support often includes IT asset and change management, helping admins with procurement, handling backup and recovery of data and applications, monitoring and analyzing logs and other performance monitoring tools and following established support workflows and processes.
Applications. Businesses rely on software to perform work. Some applications, such as email server applications, are procured and deployed by third parties. But many organizations retain a staff of skilled developers that create the applications and interfaces -- such as application programming interfaces -- needed to deliver critical business capabilities and services. Applications might be coded in a wide array of popular programming languages and integrated with other applications to create smooth and seamless interactions between different applications. Developers might also be tasked with creating interactive business websites and building mobile applications. The trend toward agile or continuous development paradigms requires developers to be increasingly involved with IT operations, such as deploying and monitoring applications.
Compliance. Businesses are obligated to observe varied government and industry-driven regulatory requirements. IT staff play a major role in securing and monitoring access to business data and applications to ensure that such resources are used according to established business governance policy that meets regulatory requirements. Such staff are deeply involved with security tasks and routinely interact with legal and business teams to prevent, detect, investigate and report possible breaches.
It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2168 2024-06-01 20:32:53
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2170) Internet Service Provider
Gist
An internet service provider (ISP) is a company that provides access to the internet. ISPs can provide this access through multiple means, including dial-up, DSL, cable, wireless and fiber-optic connections.
A variety of companies serve as ISPs, including cable providers, mobile carriers, and telephone companies. In some cases, a single company may offer multiple types of service (e.g., cable and wireless), while in other cases, a company may focus on just one type of service (e.g., fiber-optic). Without an ISP, individuals and businesses could not reach the internet and the opportunities it provides.
Summary
What Is an Internet Service Provider (ISP)?
An Internet service provider (ISP) is any company that provides Internet access to consumers and businesses. The Internet is provided through a variety of channels, including cable, DSL, fiber optics, dial-up, and wireless, with most ISPs offering all options. Most large telecommunication companies, such as mobile and cable companies, are ISPs.
ISPs make it possible for their customers to surf the web, shop online, conduct business, and connect with family and friends—all for a fee. ISPs may also provide other services, including email services, domain registration, web hosting, and browser packages.
An ISP may also be referred to as an information service provider, a storage service provider, an Internet network service provider (INSP), or any combination of these three based on the services offered by the company.
KEY TAKEAWAYS
* An Internet service provider (ISP) is a company that provides web access to businesses and consumers.
* ISPs may also provide other services such as email services, domain registration, web hosting, and browser services.
* An ISP is considered to be an information service provider, storage service provider, Internet network service provider (INSP), or a mix of all of them.
* Internet use has evolved from only those with university or government accounts having access to nearly everyone having access, whether it’s paid or free.
* Access has gone from dial-up connections to high-speed broadband technology.
Understanding Internet Service Providers (ISPs)
Internet service was originally limited to government agencies and specific university departments. The technology was developed to provide access to the general public through the World Wide Web in the late 1980s. Initially, consumers were able to gain limited access through a few ISPs—America Online (AOL) being one of the most recognized names at the time—that used dial-up connections using a phone line.
The number of ISPs increased to several thousand during the mid-1990s, and the boom was on. As the options for connectivity increased and speeds moved away from slower dial-up connections, the Internet economy was born. Providers developed more advanced technology, allowing customers high-speed access via broadband technology through cable and digital subscriber line (DSL) modems.
Behind all of this was a multilayered web of connections. Local ISPs sold access to customers but paid larger ISPs for their own access. These larger ISPs, in turn, paid even larger ISPs for access. The trail leads to Tier 1 carriers that can reach every network access point without having to pay for access. These Tier 1 companies own the infrastructure in their region.
Internet service providers provide their customers with access to the Internet—plain access providers just handle the traffic between the individual and the Internet as a whole. But there may also be other services bundled in depending on the customer’s location and availability. Some of these services include:
* Email services
* Web hosting services
* Domain registration
* Browser and software packages
Details
What is an ISP?
An ISP (internet service provider) is a company that provides individuals and organizations access to the internet and other related services. An ISP has the equipment and the telecommunication line access required to have a point of presence on the internet for the geographic area served.
ISPs make it possible for customers to access the internet while also providing additional services such as email, domain registration and web hosting. ISPs may also provide different internet connection types, such as cable and fiber. Connections can also come in the form of high-speed broadband or non-broadband. The Federal Communications Commission (FCC) states that to be considered high-speed, a connection must have download speeds of at least 25 megabits per second (Mbps) and upload speeds a minimum of 3 Mbps.
An ISP is also sometimes referred to as an internet access provider. ISP is also sometimes used as an abbreviation for independent service provider to distinguish a service provider that is a separate company from a telephone company.
How do ISPs work?
ISPs are connected to one or more high-speed internet lines. Larger ISPs have their own high-speed leased lines, so they are less dependent on telecommunications services and can provide better service to their customers.
ISPs also keep thousands of servers in data centers -- the number of servers depends on their internet service area. These large data centers manage all customer traffic. Multiple ISPs are also connected to large backbone routing centers.
ISPs are grouped into the following three tiers:
* Tier 1 ISPs. These ISPs have the most global reach and own enough physical network lines to carry most traffic on their own. They also negotiate with other tier 1 networks to allow free traffic to pass through to other tier 1 providers. Tier 1 ISPs typically sell network access to tier 2 ISPs.
* Tier 2 ISPs. These ISPs have regional or national reach and are service providers that connect tier 1 and tier 3 ISPs. They have to purchase access to larger tier 1 networks, but are peers with other tier 2 ISPs. Tier 2 networks focus on consumer and commercial customers.
* Tier 3 ISPs. These ISPs connect customers to the internet using another ISP's network. Tier 3 ISPs use and pay higher-tier ISPs for access to internet services. They focus on providing internet access to local businesses and consumer markets.
ISPs and the different types of services
ISPs provide the following internet services:
* Cable. This service uses coaxial cable -- the same type of cable that delivers TV. Cable internet has low latency, which is good for users who need less delay or lag time. Cable has a download speed of 10 to 500 Mbps and an upload speed of 5 to 50 Mbps.
* Fiber. Fiber internet uses fiber optic cable to transmit data to provide much faster speeds compared with cable or digital subscriber line (DSL). Fiber has download speeds of 250 to 1,000 Mbps and upload speeds of 250 to 1,000 Mbps. Fiber is good for online gamers and other heavy internet users.
* DSL. DSL connects users to the internet using a telephone line. It is widely available, but is slowly being replaced by more reliable broadband connections such as cable and fiber. DSL is slower and offers download speeds of 5 to 35 Mbps and upload speeds of 1 to 10 Mbps. It is a good option for users in rural areas and those who mainly surf the web or stream TV on only one device.
* Satellite. Satellite internet access works through the use of communication satellites. Ground stations relay internet data as radio waves to and from satellites that are likely in low Earth orbit and to farther ground stations. Satellite is slower, with download speeds of 12 to 100 Mbps and upload speeds of 3 Mbps, but it is a good option for users in remote areas.
Most ISPs offer a combination of these services.
What are examples of ISPs?
According to independent research by BroadbandNow and data from the FCC, there are more than 2,900 ISPs in the U.S. These ISPs offer a variety of services. The top five ISPs by estimated population covered include HughesNet, Viasat Internet, AT&T Wireless, Verizon and T-Mobile.
To break this down based on the tiers examined above, tier 1 ISPs include the following U.S.-based companies:
* AT&T
* CenturyLink
* Sprint
* Verizon
Tier 2 ISPs include the following companies:
* Comcast
* Cox Communications
* CTS Telecom
Tier 3 ISPs include smaller regional and local providers.
How to choose an ISP
Users should choose an ISP based on several factors, including the following:
* Coverage area. Which providers offer service to the user's region? If the user lives in a rural area, there may be limited options.
* Types of services offered. In addition to cable, fiber, DSL or satellite, does the ISP offer online security? Free email access? Hosting for websites? What about mesh Wi-Fi? Be sure the ISP's offerings match the user's needs.
* Download and upload speeds. Will the user be gaming online or working from home and using video teleconferencing? Both require different levels of service. For example, at least 25 Mbps of bandwidth is needed to stream 4K video.
* Pricing. Does the ISP bundle services such as internet, phone and TV, and if so, does combining services save money? Are there any data caps? What about equipment costs? Is there a contract?
Additional Information
An Internet service provider (ISP) is an organization that provides a myriad of services related to accessing, using, managing, or participating in the Internet. ISPs can be organized in various forms, such as commercial, community-owned, non-profit, or otherwise privately owned.
Internet services typically provided by ISPs can include internet access, internet transit, domain name registration, web hosting, and colocation.
It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2169 2024-06-02 18:00:10
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2171) Doctor of Medicine
Summary
Doctor of Medicine (abbreviated M.D., from the Latin Medicinae Doctor) is a medical degree, the meaning of which varies between different jurisdictions. In the United States, and some other countries, the M.D. denotes a professional degree. This generally arose because many in 18th-century medical professions trained in Scotland, which used the M.D. degree nomenclature. In England, however, Bachelor of Medicine, Bachelor of Surgery (M.B.B.S.) was used and eventually in the 19th century became the standard in Scotland too. Thus, in the United Kingdom, Ireland and other countries, the M.D. is a research doctorate, honorary doctorate or applied clinical degree restricted to those who already hold a professional degree (Bachelor's/Master's/Doctoral) in medicine. In those countries, the equivalent professional degree to the North American, and some others' usage of M.D. is still typically titled Bachelor of Medicine, Bachelor of Surgery.
History
The first medical degrees were awarded by the Schola Medica Salernitana around the year 1000, including to women such as Trota of Salerno. The degrees received legal sanction in 1137 by Roger II of Sicily and in 1231 by Emperor Federico II, in the Constitution of Melfi. In the titles XLIV-LXXXIX of the third book of the Constitutions of 1231, it was established that the activity of a physician (medicus) could only be carried out by physicians holding a medical degree, the Licentia Medendi (license to practice medicine), by the Schola Medica Salernitana (the only school in the kingdom authorized to award degrees in medicine). This degree was awarded after a curriculum composed of three years of study of logic, five years of medical studies, an examination of a commission composed of the professors of the university, a one-year apprenticeship with an expert doctor, and a final examination before the commissioners of the Royal Curia and the Provincial Curias.
In 1703, the University of Glasgow's first medical graduate, Samuel Benion, was issued with the academic degree of Doctor of Medicine.
University medical education in England culminated with the MB qualification, and in Scotland the M.D., until in the mid-19th century the public bodies who regulated medical practice at the time required practitioners in Scotland as well as England to hold the dual Bachelor of Medicine and Bachelor of Surgery degrees (MB BS/MBChB/MB BChir/BM BCh etc.). North American medical schools switched to the tradition of the ancient universities of Scotland and began granting the M.D. title rather than the MB beginning in the late 18th century. The Columbia University College of Physicians and Surgeons in New York (which at the time was referred to as King's College of Medicine) was the first American university to grant the M.D. degree instead of the MB.
Early medical schools in North America that granted the Doctor of Medicine degrees were Columbia, Penn, Harvard, Maryland, and McGill. These first few North American medical schools that were established were (for the most part) founded by physicians and surgeons who had been trained in England and Scotland.
In most countries having a Doctor of Medicine degree does not mean that the individual will be allowed to practice medicine. Typically a physician must go through a year of general medical education in a hospital as an intern and then a residency for at least three years in a specific field of medicine and then take some form of licensing examination in their jurisdiction.
Additional Information
When you say that you are going to see a doctor, you may be referring to two types of medical professionals: MDs and DOs. Each title refers to the type of degree and licensing the doctor has. Both MDs and DOs have similar training and duties, but they differ in a few key areas.
What Is an MD?
MD stands for doctor of medicine. MDs are allopathic doctors. That means they treat and diagnose conditions using conventional medical tools like x-rays, prescription drugs, and surgery. Allopathic medicine is also called conventional or mainstream medicine.
MDs can choose to be broad practitioners and work as family medicine or primary care doctors. They can also specialize in several different areas requiring further education including:
* Surgery
* Specific body parts or organs
* Psychiatry
* Geriatric medicine
* Pediatrics
What Is a DO?
DO stands for doctor of osteopathic medicine. They use the same conventional medical techniques as MDs but with a few other methods. DOs tend to focus more on holistic health and prevention. In holistic health, all parts of a person, including their mind, body, and emotions, are considered during the treatment. They also use a system of physical manipulations and adjustments to diagnose and treat people.
Over half of DOs choose to work in primary care, but they can also choose to specialize in another area, just like MDs.
It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2170 2024-06-04 15:29:52
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2172) Pacemaker
Gist
A pacemaker is a small, battery-powered device that prevents the heart from beating too slowly. You need surgery to get a pacemaker. The device is placed under the skin near the collarbone. A pacemaker also is called a cardiac pacing device. There are different types of pacemakers.
Summary
A pacemaker is a small of pacemakerevice used to treat some arrhythmias. During an arrhythmia, the heart can beat too fast, too slow, or with an irregular rhythm. Pacemakers send electrical pulses to help your heart beat at a normal rate and rhythm. Pacemakers can also be used to help your heart chambers beat in sync so your heart can pump blood more efficiently to your body. This may be needed if you have heart failure.
You may need a temporary (short-term) or permanent (long-term) pacemaker. A temporary pacemaker is normally inserted through a vein in the neck and remains outside your body. A permanent pacemaker is placed in your chest or abdomen. This topic focuses on permanent pacemakers.
To get a pacemaker, you may need to stay in the hospital for a few hours or overnight. Once you are back home, your doctor may check your pacemaker remotely and schedule regular visits with you to check its activity.
Many people with pacemakers can return to their regular activities within a few days. You may need to avoid certain electrical devices or devices that have strong magnetic fields.
Details
A pacemaker is a small battery-operated device that helps the heart beat in a regular rhythm. Traditional pacemakers have three parts: a generator, wires (leads) and sensors (electrodes). Some newer pacemakers are wireless.
It produces electrical impulses to help control abnormal heartbeats. It's implanted under the skin through a small incision on your chest just under the collarbone or sometimes in the stomach area.
The traditional pacemaker is connected to your heart through tiny wires (leads). These are implanted at the same time. The impulses flow through these wires to your heart.
The sensors (electrodes) at the end of the wires detect abnormal heartbeats and deliver electrical impulses to return your heart to its normal rhythm.
There are different types of traditional pacemakers:
* Single-lead pacemakers use one lead usually placed in the right ventricle (the lower right chamber of your heart).
* Dual-lead pacemakers use one lead in the right atrium and one lead in the right ventricle.
* Biventricular pacemakers (also called cardiac resynchronization therapy or CRT) use three leads. They are placed in the right atrium, right ventricle and left ventricle.
Wireless pacemakers are smaller than traditional ones. The pulse generator and electrodes are all in one device.
Placement of the pacemaker doesn't require surgery. It's placed inside your heart through a catheter (small tube) inserted through one of your veins. Once it's in place, the pacemaker sends impulses to the right ventricle.
Why do I need one?
Your doctor may recommend a pacemaker to make your heart beat more regularly if:
* Your heartbeat is too slow and often irregular.
* Your heartbeat is sometimes normal and sometimes too fast or too slow.
How does a pacemaker work?
The sinus node is the heart's natural pacemaker. It's a small mass of specialized cells in the top of the right atrium (upper chamber of the heart). It produces the electrical impulses that cause your heart to beat.
A chamber of the heart contracts when an electrical impulse or signal moves across it. For the heart to beat properly, the signal must travel down a specific path to reach the ventricles (the heart's lower chambers).
When the heart's natural pacemaker is defective, the heartbeat may be too fast, too slow or irregular. Rhythm problems also can occur because of a blockage or abnormality of your heart's electrical pathways.
An artificial pacemaker replaces the heart's defective natural pacemaker functions. Most pacemakers work only when they’re needed (demand pacemakers).
* Demand pacemakers have a sensing device. It shuts the pacemaker off if the heartbeat is above a certain rate.
* When the heartbeat is slower than the pacemaker rate, the sensing device turns the pacemaker on again.
* The sensors (electrodes) at the end of the wires (leads) detect abnormal heartbeats and deliver electrical impulses to return your heart to its normal rhythm.
Additional Information
A pacemaker is an electric medical device that’s generally about the size of a matchbox. A surgeon implants it under your skin to help manage irregular heartbeats called arrhythmias. Pacemakers can also be used to treat some types of heart failure.
Typically, the electrical signal that causes your heart to beat starts at an area of your heart called the sinoatrial (SA) node. The SA node is your heart’s natural pacemaker. Electrical signals generated by the SA node travel from the top of the heart to the bottom in a synchronized fashion, leading to a heartbeat.
In some situations, there are problems with this electrical signaling, which can lead to a heartbeat that’s too fast (tachycardia), too slow (bradycardia), or otherwise irregular. This is an arrhythmia. A pacemaker generates electrical impulses that help your heart beat at a normal rate, rhythm, or both.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2171 2024-06-04 20:52:18
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2173) Purchasing Power Parity
Gist
Purchasing power parity (PPP) is an economic theory of exchange rate determination. It states that the price levels between two countries should be equal.
This means that goods in each country will cost the same once the currencies have been exchanged. For example, if the price of a Coca Cola in the UK was 100p, and it was $1.50 in the US, then the GBP/USD exchange rate should be 1.50 (the US price divided by the UK’s) according to the PPP theory.
However, if you were then to look at the market exchange rate of the GBP/USD pair, it is actually closer to 1.25. The discrepancy occurs because the purchasing power of these currencies is different. As with any asset, there is the real value of a currency and the notional value, which financial markets trade at. The aim of the PPP measurement is to make comparisons between two currencies more valid, by adjusting for local purchasing power differences.
Summary
Purchasing power parity (PPP), a measure of the relative value of currencies that compares the prices of purchasing a fixed basket of goods and services in different countries. PPPs can be useful for estimating a more consistent and accurate comparison between different countries’ gross domestic product (GDP), cost of living, and other quality of life measures than using the market exchange rates of currencies. PPPs are often expressed in terms of the U.S. dollar.
When comparing the size of different countries’ economies or the relative standard of living, it is helpful to understand how those countries’ currencies compare with each other. One way this can be done is by using the market exchange rate for those currencies: simply stated, if one goes to a bank to exchange currency, how much of one currency can be purchased for a given amount of the other. However, these market exchange rates can be volatile, sometimes changing quickly in ways that do not necessarily reflect changes in the growth of economies. For example, in August 2008 the British pound sterling (GBP) was worth about $1.82 (U.S.). Two months later, it was worth about $1.54, an approximate drop of 18 percent. However, Great Britain did not experience an 18-percent increase in prices during that time. The market change in exchange rate did not reflect the experiences of American and British consumers. Instead, it reflected the behaviour of investors and institutions in reacting to economic news, such as changes in interest rates or forecasts about expected growth.
For many countries, the difference between exchange rates and PPP estimates is relatively small. However, when making comparisons between rich countries and developing countries, GDP based on PPP can dramatically increase the estimated size of developing economies, usually by two to four times. For example, using the market exchange rate, the GDP of India in 2019 was estimated to be about $2.8 trillion, just 13 percent of the United States’ $21.4 trillion. However, using PPP estimates, India’s GDP in 2019 was closer to $9.5 trillion—roughly 44 percent of the U.S. GDP. Globally, estimates of GDP based on market exchange rates indicated that in 2020 high-income countries accounted for 63 percent of the world economy, with middle-income countries collectively accounting for 36 percent. However, PPP-based estimates of GDP put middle-income countries collectively on top, with 52 percent of the global economy, compared with 47 percent for high-income countries.
These dramatic differences stem from another drawback of market exchange rates—they are based solely on the value of internationally traded goods. While these goods are important in determining the strength of an economy, as they include valuable commodities and many consumer goods, there are some goods and many services that cannot be traded on international markets. For example, a haircut in the United States may be more expensive than a haircut in India because the United States is a relatively wealthier country where people tend to be paid more for their labour. Because it is impractical for Americans to fly to India for every haircut, they are unable to take advantage of these lower prices, thus, there is a persistent gap in the price that affects the real value of the Indian rupee.
To estimate the local spending power of a currency more accurately, economists compare the relative purchasing power of the currencies more directly by comparing the price of a fixed selection of goods and services that represent the spending of individuals and institutions within a country. This “basket of goods” method, in which the cost of a fixed selection of goods and services over time is determined, is similar to how economists estimate inflation. These calculations are difficult and can be controversial as economists decide which goods and services to include in the “basket,” in what proportion to include them, and whether those products and services selected from each economy can be considered sufficiently equivalent to make a fair comparison, all of which poses a risk of creating an analysis using skewed data sets.
Gathering the amount of data required about prices across hundreds of countries to measure PPP can be a laborious task; thus, in 1968 the United Nations and the University of Pennsylvania established the International Comparison Program (ICP) to better help gather and organize comparative price data. The ICP conducts global price surveys to produce PPP estimates. In the 2017 cycle, it gathered prices on hundreds of goods and services from 176 different economies. That data was then analyzed based on the percentage of spending allocated to a specific item in a given economy. The Economist magazine offers a different, much less rigorous, approach, simplifying comparisons by focusing on a single good—the Big Mac hamburger from the fast-food chain McDonald’s. This “Big Mac index” is simply the price of a McDonald’s hamburger around the world, serving as an amusing approximation of a PPP estimate.
Details
Purchasing power parity (PPP) is a popular macroeconomic analysis metric used to compare economic productivity and standards of living between countries.
PPP involves an economic theory that compares different countries' currencies through a "basket of goods" approach. That is, PPP is the exchange rate at which one nation's currency would be converted into another to purchase the same and same amounts of a large group of products.
According to this concept, two currencies are in equilibrium—their currencies are at par—when a basket of goods is priced the same in both countries, taking into account the exchange rates.
KEY TAKEAWAYS
* Purchasing power parity (PPP) is a popular metric used by macroeconomic analysts that compares different countries' currencies through a "basket of goods" approach.
* PPP allows economists to compare economic productivity and standards of living between countries.
* Some countries adjust their gross domestic product (GDP) figures to reflect PPP.
* Some feel that PPP does not reflect reality due to differences in local costs, taxes, tariffs, and competition.
How PPP Is Used
To make a meaningful comparison of prices across countries, a wide range of goods and services must be considered. However, the one-to-one comparison is difficult to achieve due to the sheer amount of data that must be collected and the complexity of the comparisons that must be drawn.
To help facilitate this comparison, the University of Pennsylvania and the United Nations joined forces to establish the International Comparison Program (ICP) in 1968.
Users of PPP
With this program, the PPPs generated by the ICP have a basis in a worldwide price survey that compares the prices of hundreds of various goods and services. Thus, the program helps international macroeconomists estimate global productivity and growth.
Every few years, the World Bank releases a report that compares the productivity and growth of various countries in terms of PPP and U.S. dollars.
Both the International Monetary Fund (IMF) and the Organization for Economic Cooperation and Development (OECD) use weights based on PPP metrics to make predictions and recommend economic policy.
Their recommendations can have an immediate short-term impact on financial markets.
Some forex traders use PPP to find potentially overvalued or undervalued currencies. And investors who hold stocks or bonds of foreign companies may use the survey's PPP figures to predict the impact of exchange-rate fluctuations on a country's economy, and thus on their investment.
The PPP exchange rate is used to convert the local currency of a target nation into a common currency applicable to all nations. Normally, this common currency is the US dollar or what's called the International dollar, a currency designed to serve as a baseline.
Pairing PPP With Gross Domestic Product
In contemporary macroeconomics, gross domestic product (GDP) refers to the total monetary value of the goods and services produced within one country. Nominal GDP calculates the monetary value in current, absolute terms. Real GDP adjusts the nominal gross domestic product for inflation.
Some accounting goes even further, adjusting GDP for the PPP value. This adjustment attempts to convert nominal GDP into a number more easily compared between countries with different currencies.
Example
To better understand how GDP paired with purchase power parity works, suppose it costs $10 to buy a shirt in the U.S., and it costs €8.00 to buy an identical shirt in Germany. To make an apples-to-apples comparison, we must first convert the €8.00 into U.S. dollars. If the exchange rate was such that the shirt in Germany costs $15.00, the PPP would, therefore, be 15/10, or 1.5.
In other words, for every $1.00 spent on the shirt in the U.S., it takes $1.50 to obtain the same shirt in Germany when buying it with the euro.
Additional Information
Purchasing power parity (PPP) is a measure of the price of specific goods in different countries and is used to compare the absolute purchasing power of the countries' currencies. PPP is effectively the ratio of the price of a market basket at one location divided by the price of the basket of goods at a different location. The PPP inflation and exchange rate may differ from the market exchange rate because of tariffs, and other transaction costs.
The purchasing power parity indicator can be used to compare economies regarding their gross domestic product (GDP), labour productivity and actual individual consumption, and in some cases to analyse price convergence and to compare the cost of living between places. The calculation of the PPP, according to the OECD, is made through a basket of goods that contains a "final product list [that] covers around 3,000 consumer goods and services, 30 occupations in government, 200 types of equipment goods and about 15 construction projects"
It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2172 2024-06-05 15:56:39
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2174) Venetian Blinds
Gist
A cover for a window, usually made of thin, horizontal strips of wood, plastic, or metal, that can be moved in order to change the amount of light that is allowed in.
Details
A window blind is a type of window covering. There are many different kinds of window blinds which use a variety of control systems. A typical window blind is made up of several long horizontal or vertical slats of various types of hard material, including wood, plastic or metal which are held together by cords that run through the blind slats. Vertical blinds run along a track system which can tilt open and closed and move side-to-side. Window blinds can be manoeuvred with either a manual or remote control by rotating them from an open position, with slats spaced out, to a closed position where slats overlap and block out most of the light. There are also several types of window coverings, called shades, that use a single piece of soft material instead of slats.
The term window blinds can also be used to describe window coverings more broadly. In this context window blinds include almost every type of window covering, whether it is a hard or soft material; i.e. shutters, roller shades, cellular shades (also called honeycomb shades), wood blinds, Roman shades, standard vertical, and horizontal blinds (also called Venetians). In the United Kingdom, awnings are sometimes called blinds or shades.
Overview
Window blinds are generally sold as either ready-made or made to measure. As the names suggest, blinds that are ready-made are manufactured to set sizes based on typical window dimensions, whereas blinds that are made to a measurement are cut to a specific width and drop to match the window. The advantage of ready-made blinds is their availability and cost, whereas blinds that are made to measure will be more expensive but better fit the dimensions of a window.
Aside from coming in different dimensions, window blinds can also come in a variety of different styles, materials, colours and patterns. Below is a list of several popular styles of blinds:
* Panel
* Pleated
* Roller
* Roman
* Venetian
* Vertical
* Wooden
Window blinds can be drawn manually using a cord, or automated through motorization. Controls for motorized blinds can be from a wall switch or keypad, remote control, or computer, eliminating the need for cords and allowing control of otherwise inaccessible windows. A number of modern homes are integrating blind control with central C-Bus solutions. This control provides ease of use and is effective for controlling blind operation to reduce heat loss during winter or minimize heat from the sun during summer.
Types:
Panel
Panel blinds, sometimes referred to as Japanese blinds as they are based on Japanese shōji, are thin blinds in a panel shape that run along a track. Almost any fabric or paper can be employed, although 90% of all shoji blinds use white polyester to imitate 'washi' Japanese paper.
Cellular shades
Cellular shades or cellular blinds, sometimes referred to as honeycomb shades, are a type of window blind made of a long and continuous fabric with a cellular structure when opened and fold onto themselves when closed. The fabric is often made from soft paper or cloth-like material and is available in a variety of different structures including single cell, double cell or triple cell. Cellular blinds work by trapping air inside the cell structure once opened and create a barrier between the window surface and the room. Due to the unavailability of standardized tests, no ranking system currently exists to compare the efficacy of these blinds.
Windows and doors make up for almost one-third of a home's total thermal loss, according to the Department of Energy (United Kingdom). This applies to heat loss in winter as well as entry of undesired heat in summer. When air inside the room comes in contact with windows, it is cooled or warmed. By convection, this air then circulates around the room. Cell shapes in the blinds hold trapped air and create a barrier between the window surface and the room, thus lessening the transfer of heat. Shades, however, provide only slight control of air infiltration.
In common with all blinds, cellular shades can reduce solar gain in summer and provide room darkening or blackout for sleeping. Like most other window treatments, they are raised and lowered with a string. Cordless cellular shades are available to reduce the risk of strangulation for small children. One may also have the option of lowering the top of the shade down, and/or the bottom of the shade up; commonly referred to as a Top-Down-Bottom-Up mechanism.
Roman
Roman shades are a type of window blind used to help block out the sun. Although often called blinds, these are actually referred to as "shades" in the window covering industry. They are often referred to as Romans or Roman blinds in the UK. When opened, the Romans stack up evenly; when covering the full window height, they are smooth without overlapping.
Roman blinds can be purchased with a blackout lining on the back to fully block out sunlight. However, there will always be small light gaps on the edges of the blinds if mounted on the inside of the window frame or peeking out from behind the blind if mounted on the frame around the window.
Unlike other blinds, such as certain fabrics used for Roller Shades, Vinyl Vertical blinds, or Vinyl Horizontal blinds, Roman Shades are not an ideal option for areas with a lot of moisture, such as bathrooms or windows above the kitchen sink.
Roller
Roller blinds are a type of window blind that is typically made from a polyester fabric wrapped around a plastic or metal roller. The roller may either be exposed or enclosed inside of a frame and can be placed at the top of the window recess or outside of the recess. To control the roller blind there is typically a chain or string on either side of the blind. When the side chain is pulled one direction the roller will raise, and if pulled in the opposite direction it will lower instead.
Some manufacturers also produce a version of roller blinds with two layers of fabric, sometimes referred to as double roller blinds, for even greater control of light filtration through a window. Typically, one layer will be made of a sheer fabric that can be used to reduce glare, with a second layer that typically includes a blackout lining for even greater filtration when necessary.
Venetian
A Venetian blind is a type of window blind made from overlapping horizontal slats that are typically lowered and drawn together by pulling a cord. The slats are typically manufactured using a rigid material such as aluminium, plastic, or wood and move in unison through a series of wires that run through the blinds.
In the late 19th and early 20th centuries, Venetian blinds were widely adopted in office buildings to regulate light and air. A large modern complex in the US that adopted Venetian blinds was Rockefeller Center's RCA Building (better known as the Radio City building) in New York City, completed in the 1930s. One of the largest orders for Venetian blinds ever placed was to the Burlington Venetian Blind Co., of Burlington, Vermont, which supplied blinds for the windows of the Empire State Building in New York City.
Venetian blinds
In 1994, a design for Venetian blinds integrated with window glass panels was patented. This new type of blind overcomes the problems related to damaging and fouling. Usually, magnets are used for motor transmission in order to preserve the sealing inside the insulating glass.
Vertical
Unlike horizontal blinds, vertical blinds are less likely to collect dust because they stand vertically. Since they draw to the side rather than lifting and lowering, they are easier and faster to operate. They operate best on patio doors and sliding windows that slide from side to side. In the 1970s there were few choices of fabric- usually beige or white, which had to have stiffener embedded to prevent fraying, rather like on roller blinds fabric but using a thicker textile.
Vertical blinds became available in flat plastic (PVC), fabric, embossed PVC, also S-curved slats. A more modern modification is to offer them with wood trim at the top and bottom—sometimes midway as well—and these are usually described as "Japanese Vertical blinds" because they are often coordinated with Japanese style Shoji blinds using the same timber. Vertical blinds were most popular in the UK during the 1990s, since then sales have slowed as they lost popularity with a younger generation.
Stationary vertical blinds are hung in the doorways of some homes and businesses which generally leave the door open. Movement of the blind may signal a change in airflow, or someone entering the doorway. More commonly, however, these vertical blinds are made of thick plastic. In the cold rooms of food businesses, this slows the heat leakage into the cold room. In warmer climates, vertical blinds discourage flies and some other insects from entering the building. In certain areas of the UK window blinds are used to disguise the fact that offices have PCs in them and are used as a burglary deterrent.
Others
Other varieties of window blinds include mini blinds (typically aluminum, Venetian-Style blinds with very narrow slats, usually 25 mm or 1 inch wide), micro blinds (usually 13 mm or 1⁄2 inch wide), louvers, jalousies, brise soleil and pleated blinds.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2173 2024-06-06 15:12:11
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2175) Master of Engineering
Gist
To be awarded the graduate degree of Master of Engineering (MEng) with specification of the field in which the student has specialized, the student must have completed satisfactorily at least 66 units of subject credit (including at least 42 graduate units) and a thesis which collectively constitute a structured program of at least 90 units acceptable to the department of the School of Engineering in which the student is enrolled. The candidate must also have been in residence for a minimum of one regular term.
Details
A Master of Engineering (abbreviated MEng, ME, M.E. or M.Eng.) is a professional master's degree in the field of engineering.
International variations
Australia
In Australia, the Master of Engineering degree is a research degree requiring completion of a thesis. Like the Master of Philosophy (M.Phil.), it is considered a lesser degree than Doctor of Philosophy (Ph.D.). It is not to be confused with Master of Engineering Science, Master of Engineering Studies or Master of Professional Engineering which are coursework master's degrees. Exceptions are Monash University which awards a Master of Engineering Science by either research or coursework, the University of Melbourne which offers a Master of Engineering by coursework, and the University of Tasmania which offer a Master of Engineering Science by research.
Finland
There are two distinct degrees in Finland, a taught university degree (diplomi-insinööri) and a polytechnic master's degree's (insinööri (ylempi AMK)). While the former is translated as "Master of Science in Technology", the term "Master of Engineering" is predominantly used by Universities of Applied Sciences, which offer master's degree programs to holders of polytechnic bachelor's degrees (insinööri (amk)). As European Bologna process directs, in order to get an M. Eng. degree, B.Eng. engineers have to additionally study full-time one or two years and finalize a master's thesis. Most of the M. Eng. degree programs are taught in Finnish, but some Swedish and English language programs also exist.
France
In France there are two distinct kinds of Master of Engineering. A master's degree taught in university and an engineer degree Diplôme d'Ingénieur taught in engineer schools, which is a parallel education system of university, named Grande école. Master of engineering and engineer's degree are both equal in term of level education, and generally leads to the same positions. The engineer's title in France is strictly protected and can be used only after a successful graduation in an Engineer School accredited by state. While a university's master's degree of engineering is a grade which does not give the right to use the Engineer's title, even if position's level and responsibilities are same. For the same reason, Bachelor of Engineering does not allow a graduate to be called "Engineer" or to work as an engineer. To work as an engineer requires 5 years of education in university or Engineer's school and using the title of engineer requires graduation from an engineer school.
Germany
In Germany, the local engineer's degrees (Diplomingenieur (Dipl.-Ing.), a first degree after five years of study at a university and Dipl.-Ing. (FH), the engineering degree offered by Fachhochschulen after four years of study) were abolished in most universities and "Fachhochschulen" in 2010 and were replaced by postgraduate master's degrees (M.Sc. and M.Eng.).
The first Master of Engineering courses were introduced in Germany in 2000 as result of the Bologna process. This type of master's degree is usually offered by Fachhochschulen (Universities of Applied Sciences) and a few smaller German universities and is typically a two-year program (fachhochschulen and universities) with application-oriented coursework and an applied or research thesis.
The entry requirement is the successful completion of a bachelor's degree or an equivalent from before the Bologna process, with good marks.
The nine leading German technical universities (Group of TU9), like most European universities of technology, prefer awarding the Master of Science degree for completing engineering science studies in a master's program.
New Zealand
In New Zealand, the Master of Engineering degree is generally a research based degree requiring completion of a thesis in key universities (University of Auckland, University of Canterbury, etc.). Similar to the UK's Master of Philosophy (M.Phil.) in engineering or technology, it is considered a lesser degree than Doctor of Philosophy (Ph.D.) and a higher degree than a coursework master. It is not to be confused with Master of Engineering Studies which is coursework master's degree.
In Auckland University of Technology (AUT), this degree can be achieved either by completing a thesis (research pathway) or a combination of coursework and research project (coursework pathway).
Slovakia
FIIT STU Institution of Engineering and Technology (IET) accreditation for two master's degree study programs: Intelligent Software Systems (combined fields of study Software Engineering – major and Artificial Intelligence – secondary) and Internet Technologies (in the field of study Computing Engineering); three bachelor's degree study programs and two doctoral degree study programs.
United Kingdom
In the United Kingdom, the degree of Master of Engineering (MEng) is the highest award for undergraduate studies in engineering. It is the standard university-level qualification taken by people wishing to become chartered engineers registered with the Engineering Council (EngC). The MEng degree represents the minimum educational standard required to become a chartered engineer, but there are other equally satisfactory ways to demonstrate this standard, such as the completion of a BEng Honours and a subsequent postgraduate diploma, MA or MSc or through experiential learning. The UK MEng (undergraduate degree) is typically equivalent to the European Diplom Ingenieur (Dipl.-Ing.) and Civilingenjör degrees.
Universities are free to set their own entry requirements. Some universities, such as Oxford, Cambridge and some courses at Imperial only admit students to study for the MEng degree. (Their courses usually allow a student to leave with a bachelor's degree after three years. Other universities, such as the University of Greenwich, University of Surrey, Coventry University, Brunel University and Swansea University, admit students to read for BEng Honours and MEng courses and allow students to change between the two during the early years of the course. The Open University offers the MEng degree as a postgraduate qualification but requires students to complete its course within four years of completing a BEng Honours degree.
Requirements for professional registration as an Incorporated Engineer or a Chartered Engineer is based on a standard of professional competence and commitment, as set out in the professional standard UK-SPEC. Individuals generally develop these through education and working experience.
History
Since its introduction, the MEng has become the degree of choice for most undergraduate engineers, as was intended. The most common exception to this is international students who, because of the substantially higher fees they are charged, sometimes opt to take the tradition BEng/B.Sc. route where that is available. Most of the engineering institutions have now made an MEng the minimum academic standard necessary to become a Chartered Engineer. Students who graduated before the changes in the rules will still be allowed to use their bachelor's degree for this purpose and those who have earned a bachelor's degree since the changes can usually take some additional courses (known as 'further learning') over time to reach an equivalent standard to the MEng Some older universities such as Durham allow students to obtain the BEng degree after the third year before continuing on to the fourth year.
United States
In the United States, the Master of Engineering degree is generally a professional degree offered as a coursework-based alternative to the traditional research-based Master of Science. It is typically a one-year program, entered after the completion of a 4-year bachelor's degree and many universities allow students to choose between the Master of Engineering and the Master of Science.
The Master of Engineering degree is offered at many leading universities in the United States on either a full-time and part-time (weekends or evenings) basis and is considered a terminal degree in the field of engineering and is considered as a step forward in one's professional career as an engineer.
Some MEng degree programs require a scholarly project in addition to coursework. They require additional courses beyond those required for Master of Science students in order to better prepare students for professional careers. Some of them highly encourage students to participate in collaborative consulting projects. These courses may include topics such as business fundamentals, management and leadership.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2174 2024-06-07 14:24:30
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2176) MBBS
Gist
The MBBS Full Form is Bachelor of Medicine and Bachelor of Surgery. Medical institutions and universities award the MBBS, a specialist undergraduate degree in medical and surgical medicine. One of the well-known and popular medical degrees in India is the MBBS.
Summary
MBBS is the most used acronym for Bachelor of Medicine and Bachelor of Surgery. This implies that the course imparts students with complete knowledge of medical science and prepares them to perform surgeries.
The UK is regarded as one of the highly preferred study locations for Indian students aspiring to become specialist doctors after completing MBBS.
Details
A Bachelor of Medicine, Bachelor of Surgery (Latin: Medicinae Baccalaureus, Baccalaureus Chirurgiae; MBBS, also abbreviated as BM BS, MB ChB, MB BCh, or MB BChir) is a medical degree granted by medical schools or universities in countries that adhere to the United Kingdom's higher education tradition. Despite the historical distinction in nomenclature, these degrees are typically combined and conferred together. This degree is usually awarded as an undergraduate degree, but it can also be awarded at graduate-level medical institutions. The typical duration for completion is five to six years.
In contrast, a Bachelor of Medicine (MB, also abbreviated as BMed) is an undergraduate medical degree awarded by medical schools in countries following the tradition of China. The completion period for this degree is generally five to six years. The term 'Medicine' in this context encompasses the broader field of medical science and practice, rather than specifically internal medicine. Consequently, graduates with an MB degree are qualified to practise surgery. The MB degree serves as the primary medical qualification, and individuals holding it may pursue further professional education, such as a Master of Medical Science or a Doctor of Medical Science (equivalent to a PhD).
Both degrees are considered equivalent to the Doctor of Medicine degree typically conferred by universities in North America. In the United States only, some doctors opt to train in osteopathic medicine, and thus receive a Doctor of Osteopathic Medicine degree. For practical purposes, the degrees are considered to be equal.
History and nature
The degree is currently awarded in institutions in the United Kingdom and countries formerly part of the British Empire.
Historically, Bachelor of Medicine was also the primary medical degree conferred by institutions in the United States and Canada, such as the University of Pennsylvania, Harvard University, the University of Toronto, the University of Maryland, and Columbia University. Several early North American medical schools were (for the most part) founded by physicians and surgeons who had trained in England and Scotland. University medical education in England culminated with the Bachelor of Medicine qualification and in Scotland the Doctor of Medicine. In the mid-19th century, the public bodies that regulated medical practice required practitioners in Scotland and England to hold the dual Bachelor of Medicine and Bachelor of Surgery degrees. Over the course of the 19th century, North American medical schools switched to the tradition of the ancient universities of Scotland and began conferring Doctor of Medicine rather than Bachelor of Medicine.
In the countries that award bachelor's degrees in medicine, however, Doctor of Medicine denotes a holder of a junior doctorate and is reserved for medical practitioners who undertake research and submit a thesis in the field of medicine. Nevertheless, those holding Bachelor of Medicine, Bachelor of Surgery are usually referred to by the courtesy title of "Doctor" and use the prefix "Dr.", whether or not they also hold a Ph.D. or DSc. In theory, the right to the use of the title "Doctor" is conferred on the medical graduate when he or she is registered as a medical practitioner by the relevant professional body, not by the possession of the MBBS degrees.
In many countries, the degrees are awarded after an undergraduate course lasting five or six years. For example, most Chinese universities offering medical degrees provide undergraduate courses lasting six years. In some cases, a graduate in another discipline may subsequently enter a special graduate-entry medical course, reduced in duration to account for relevant material covered or learning skills acquired during the first degree. In some cases the old first-year courses (for six-year degrees) in the basic sciences of physics, chemistry, and biology have been abolished: that standard has to be reached by school examinations before entry. However, in most countries, a newly graduated Bachelor of Medicine and Surgery must spend a specified period in internship before he or she can obtain full registration as a licensed medical practitioner.
Naming
The names and abbreviations given to these degrees depend on the institution, awarding body or country, and vary widely. This is mostly for reasons of tradition rather than to indicate any difference between the relative levels of the degrees. They are considered equivalent.
If the awarding body titles the degrees in Latin, the degrees are commonly named Medicinae Baccalaureus, Chirurgiae Baccalaureus; Medicinae Baccalaureus et Chirurgiae Baccalaureus; or Baccalaureus in Medicina et in Chirurgia; abbreviated as MB ChB, MB BCh or otherwise. If titled in English, they are named Bachelor of Medicine, Bachelor of Surgery; Bachelor of Medicine and Bachelor of Surgery; or Bachelor of Medicine and Surgery; usually abbreviated as MB BS, and sometimes as BM BS, even though most MB BS-awarding institutions do not use Latin to name their degrees.
It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline
#2175 2024-06-08 15:45:57
- Jai Ganesh
- Administrator

- Registered: 2005-06-28
- Posts: 52,931
Re: Miscellany
2177) Master of Philosophy
Gist
The full form of MPhil is Master of Philosophy.
MPhil is a 2-year postgraduate level course that is offered in many specializations. Candidates who have completed a Master's degree can pursue an MPhil in the same or related fields.
Details
A Master of Philosophy (MPhil; Latin Magister Philosophiae or Philosophiae Magister) is a postgraduate degree. An MPhil may be awarded to postgraduate students after completing taught coursework and one to two years of original research, which may also serve as a provisional enrolment for a PhD programme.
Australia
In Australia, the Master of Philosophy is a research degree which mirrors a Doctorate of Philosophy (PhD) in breadth of research and structure. Candidates are assessed on the basis of a thesis. A standard full-time degree often takes two years to complete.
Belgium
In Belgium, the MPhil is a special research degree, and is only awarded by selected departments of a university, mostly in the fields of arts, social sciences, archaeology, philosophy and theology. Admission to these programmes is highly selective and primarily aimed at those students aiming for an academic career. After finishing these programmes, students normally pursue a PhD programme.
Canada
The MPhil is offered at some Canadian universities as a two-year degree involving coursework, examinations, and practice at academic writing. At some institutions, successful completion leads to a guaranteed place on a PhD course with "advanced standing", reducing the length of the PhD by a year.
India
Indian universities used to offer MPhil degrees as the most advanced master's degree in the fields of arts, science and humanities. The duration was typically two years long and included both a taught portion and an extensive research portion. Several universities offered enrolment in their integrated MPhil–PhD program and MPhil degree holders were usually exempted from some of the doctoral coursework requirement. In July 2020, the Government of India announced that, as part of its new National Education Policy, MPhils would be discontinued in India. In 2023, University Grants Commission reiterated that fresh admissions should not be done for MPhil degree, as it is not valid anymore.
Finland
In Finland, the regular master's degree filosofian maisteri translates to "Master of Philosophy". As in English, the term "philosophy" does not imply a specialization in theoretical philosophy. These degrees are regular master's degrees, not special "higher" degrees (cf. Licentiate and Doctor of Philosophy). In the past, filosofian maisteri signified that the degree was earned through actual studying, in contrast to honorary master's degrees that were granted upon application to bachelor's degree graduates.
Malaysia
In Malaysia, the MPhil degree is commonly offered in a number of older and more-established universities in Malaysia, including the University of Malaya, Multimedia University (MMU), Wawasan Open University, University of Nottingham Malaysia Campus (UNMC), Monash University Sunway Campus (MUSC) and Curtin Malaysia Campus. In most cases, the MPhil is largely a research degree, with only a minor taught component. On a case-by-case basis, candidates must pass a viva voce examination before the degree is awarded. For UNMC and MUSC, the Faculty of Engineering offers a standalone MPhil degree which will lead to the PhD.
Specifically for the University of Malaya, if the desired field of research does not belong to any of the specialized faculties, it is normally categorized under the MPhil supervised by the Postgraduate Institute.
In November 2012, the Malaysian Qualifications Agency issued programme standards for postgraduate studies in which MPhil is attributed to Master programme by research and mixed mode (coursework and research).
Netherlands
The Dutch Department of Education, Culture and Science decided in 2009 not to recognize the MPhil degree. Accordingly, Dutch universities stopped awarding this degree and now award the legally-recognized Master of Arts or Master of Science degrees instead.
Norway
In Norway, the degree of MPhil was a master's degree (180 ECTS credits) at a level equivalent to an MA or MSc However, unlike a standard MA or MSc, which have a thesis worth 60 ECTS, the MPhil has a research workload of up to 180 ECTS. Upon completion, the MPhil graduate usually qualifies for acceptance to a PhD program. Nevertheless, the MPhil is most often taken as a standalone qualification.
The MPhil degree was considered to be equivalent to US and UK PhD degrees and from the early 1900s the PhD established itself as the usual translation of Danish and Norwegian master's degrees into English. This must be seen in the context of the fact that the PhD originally designated research education in the US and eventually equivalent degrees in the UK which had a similar scope and fulfilled a similar function as the master's degree in Denmark and Norway, as the final degree taken at the beginning of a research career, while the doctorates in Denmark and Norway were often taken by middle-aged and well-established academics. In Denmark and Norway, PhD in the 20th century was therefore not necessarily or necessarily regarded as identical to a "doctorate" as understood in Denmark and Norway.
Pakistan
In Pakistan, the MPhil is one of the most advanced master's degrees offered by public and private universities in several different fields of study. This is usually a two-year full-time program which includes teaching and research that leads to the PhD. The degree of MPhil also served as a requirement to gain admission into a Doctoral program in Pakistan until early-2021.
Spain
In Spain, the MPhil degree is equivalent to the Diploma de Estudios Avanzados, or DEA. In order to obtain it, the student has to complete a full year of doctoral courses and training in research methods, as well as doing original research towards a thesis.
United Kingdom
In most UK universities, the MPhil is a research degree. The completion of an MPhil typically requires two years of full-time (or five years or more of part-time study) and the submission of coursework and a thesis comprising a body of original research undertaken by the candidate (typically 25,000 to 50,000 words). It is common for students admitted into a PhD program at a UK university to be initially registered for the degree of MPhil, and then to transfer (or upgrade) to the PhD upon successful completion of the first (or sometimes the second) year of study: this will often involve the submission of a report or dissertation by the student, and possibly an oral examination or presentation. Conversely, a PhD candidate may transfer to an MPhil programme or be awarded the degree of MPhil if they do not meet the requirements for the award of a PhD.
Usage can be different at the ancient universities. The MPhil at Oxford and Cambridge can be either a taught degree or a research degree, and may take one or two years, depending on the course. Cambridge University offers one- and two-year-long MPhil degree programs across all of its departments and faculties, although in most cases the Cambridge MPhil is a one-year taught degree. This takes the place of the MA at other universities, as the Oxbridge MA is awarded to BA graduates after a certain period without any further study. At Oxford University, the MPhil is usually a two-year master's degree. The Oxford MPhil requires a lengthy thesis in the second year and more examinations than a one-year master's degree (such as the MSc or MSt). The ancient Scottish universities, who for historical reasons award the Scottish MA upon completion of four-year first degree programs in arts and humanities subjects, differ in their use of MPhil or MLitt for postgraduate research degrees, but are slowly standardizing to the MPhil as a research degree and the MLitt as a taught degree.
United States
Most American universities do not award the Master of Philosophy degree. A few institutions, such as Yale University, Columbia University, New York University, George Washington University, The New School, and the CUNY Graduate Center, award it under certain circumstances, such as to PhD candidates when they complete their required coursework and qualifying examinations but have not yet completed and defended their doctoral dissertation. This formalizes the more colloquial "All But Dissertation" status; as such, defense of a dissertation proposal is sometimes required for conferral. Other colleges and universities, such as the University of Michigan and the University of Pennsylvania, offer a standalone MPhil as an advanced graduate degree in various fields.

It appears to me that if one wants to make progress in mathematics, one should study the masters and not the pupils. - Niels Henrik Abel.
Nothing is better than reading and gaining more and more knowledge - Stephen William Hawking.
Offline